The latest updated Cisco 200-201 exam dumps and free 200-201 exam practice questions and answers! Latest updates from leads4pass Cisco 200-201 Dumps PDF and 200-201 Dumps VCE, leads4pass 200-201 exam questions updated and answers corrected!
Get the full Cisco 200-201 dumps from https://www.leads4pass.com/200-201.html (VCE&PDF)
Latest 200-201 PDF for free
Share the Cisco 200-201 Dumps PDF for free From leads4pass 200-201 Dumps part of the distraction collected on Google Drive shared by leads4pass
https://drive.google.com/file/d/1wdj4_0430knv7XaRonVj1MCahJaFYIXU/
The latest updated Cisco 200-201 Exam Practice Questions and Answers Online Practice Test is free to share from leads4pass (Q1-Q13)
QUESTION 1
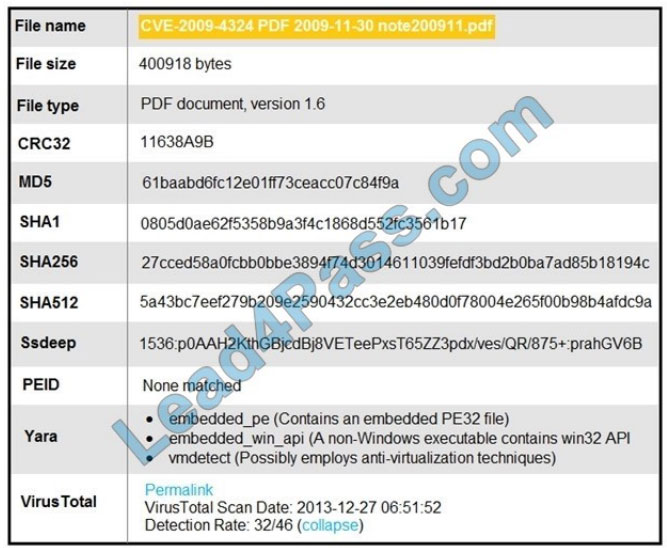
Refer to the exhibit. An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from
an email. What is the state of this file?
A. The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
B. The file has an embedded non-Windows executable but no suspicious features are identified.
C. The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
D. The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up
to date.
Correct Answer: C
QUESTION 2
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A. Untampered images are used in the security investigation process
B. Tampered images are used in the security investigation process
C. The image is tampered if the stored hash and the computed hash match
D. Tampered images are used in the incident recovery process
E. The image is untampered if the stored hash and the computed hash match
Correct Answer: BE
QUESTION 3
How does an attacker observe network traffic exchanged between two users?
A. port scanning
B. man-in-the-middle
C. command injection
D. denial of service
Correct Answer: B
QUESTION 4
Which regex matches only on all lowercase letters?
A. [a-z]+
B. [^a-z]+
C. a-z+
D. a*z+
Correct Answer: A
QUESTION 5
What specific type of analysis is assigning values to the scenario to see expected outcomes?
A. deterministic
B. exploratory
C. probabilistic
D. descriptive
Correct Answer: A
QUESTION 6
Which security principle requires more than one person is required to perform a critical task?
A. least privilege
B. need to know
C. separation of duties
D. due diligence
Correct Answer: C
QUESTION 7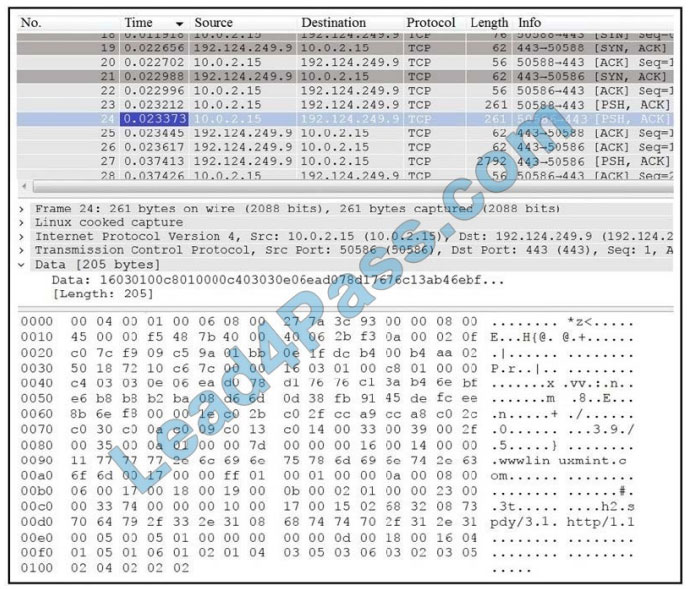
Refer to the exhibit. Which application protocol is in this PCAP file?
A. SSH
B. TCP
C. TLS
D. HTTP
Correct Answer: B
QUESTION 8
What causes events on a Windows system to show Event Code 4625 in the log messages?
A. The system detected an XSS attack
B. Someone is trying a brute force attack on the network
C. Another device is gaining root access to the system
D. A privileged user successfully logged into the system
Correct Answer: B
QUESTION 9
Which two components reduce the attack surface on an endpoint? (Choose two.)
A. secure boot
B. load balancing
C. increased audit log levels
D. restricting USB ports
E. full packet captures at the endpoint
Correct Answer: AD
QUESTION 10
How does certificate authority impact a security system?
A. It authenticates client identity when requesting an SSL certificate
B. It validates the domain identity of an SSL certificate
C. It authenticates domain identity when requesting an SSL certificate
D. It validates client identity when communicating with the server
Correct Answer: B
QUESTION 11
DRAG DROP
Drag and drop the security concept on the left onto the example of that concept on the right.
Select and Place: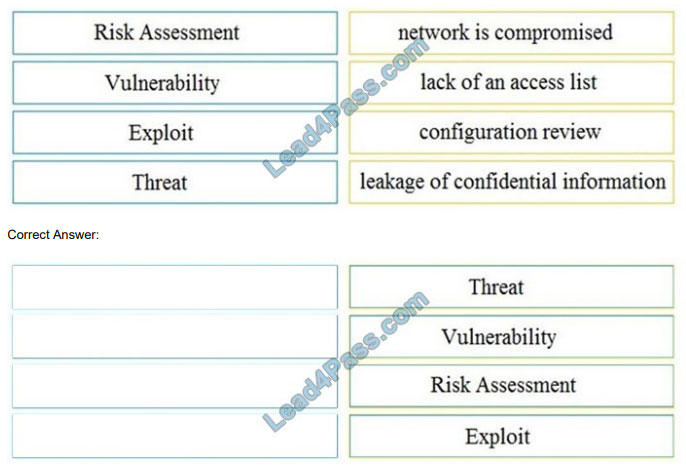
QUESTION 12
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different
bank account number?
A. integrity
B. confidentiality
C. availability
D. scope
Correct Answer: A
QUESTION 13
In a SOC environment, what is a vulnerability management metric?
A. code signing enforcement
B. full assets scan
C. internet exposed devices
D. single-factor authentication
Correct Answer: C
Vcecert shares the latest updated Cisco 200-201 exam exercise questions, 200-201 dumps pdf for free.
All exam questions and answers come from the leads4pass exam dumps shared part! leads4pass updates throughout the year and shares a portion of your exam questions for free to help you understand the exam content and enhance your exam experience!
Get the full Cisco 200-201 exam dumps questions at: https://www.leads4pass.com/200-201.html (pdf&vce)
ps.
Get free Cisco 200-201 dumps PDF online: https://drive.google.com/file/d/1wdj4_0430knv7XaRonVj1MCahJaFYIXU/


Recent Comments