
Successfully passing the Cisco 350-201 exam to obtain certification makes it easy for you to become a top talent.
“Cisco CyberOps Professional 350-201 contains many latest technologies:
Fundamentals,Techniques,Processes,Automation”
It is not a simple matter to obtain Cisco CyberOps Professional 350-201 certification: first, you need to pay the exam fee of 400 dollars, secondly, you need to learn a lot of professional knowledge for the exam, and finally, you need to take the exam. This kind of process does not guarantee that you will pass the exam. Every year, many people cannot pass the exam smoothly!
I’m not trying to discourage everyone’s confidence, I just say that the Cisco CyberOps Professional 350-201 exam is not easy! So I share 13 valid Cisco 350-201 exam questions for free to help you improve your skills and exam experience!
All the exam questions I shared are the latest updates! All 350-201 exam dumps come from leads4pass.com!
leads4pass will help you save a lot of money and help you pass the exam successfully for the first time! And we have the best exam credibility! You are not the first to need us!
Table Of Content:
- Download Cisco 350-201 exam pdf online
- Cisco 350-201 exam video from Youtube
- The latest updated Cisco 350-201 exam practice questions
- Cisco 350-201 Exam Certification Coupon Code 2021
[Cisco 350-201 exam pdf online for free] Share the Cisco 350-201 Dumps PDF for free From leads4pass 350-201 Dumps part of the distraction collected on Google Drive shared by leads4pass
https://drive.google.com/file/d/1s19V_3m7G1cpfnNm5DTJ02_zUW1j34Mw/
[Latest leads4pass 350-201 Youtube] Share the latest Cisco 350-201 exam practice questions and answers for free from Led4Pass Dumps viewed online by Youtube Videos
Cisco CyberOps Professional 350-201 exam question and answer online practice exam
QUESTION 1

Refer to the exhibit. Where does it signify that a page will be stopped from loading when a scripting attack is detected?
A. x-frame-options
B. x-content-type-options
C. x-xss-protection
D. x-test-debug
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/customize-http-security-headersad-fs
QUESTION 2
A company\\’s web server availability was breached by a DDoS attack and was offline for 3 hours because it was not
deemed a critical asset in the incident response playbook. Leadership has requested a risk assessment of the asset. An
analyst conducted the risk assessment using the threat sources, events, and vulnerabilities.
Which additional element is needed to calculate the risk?
A. assessment scope
B. event severity and likelihood
C. incident response playbook
D. risk model framework
Correct Answer: D
QUESTION 3
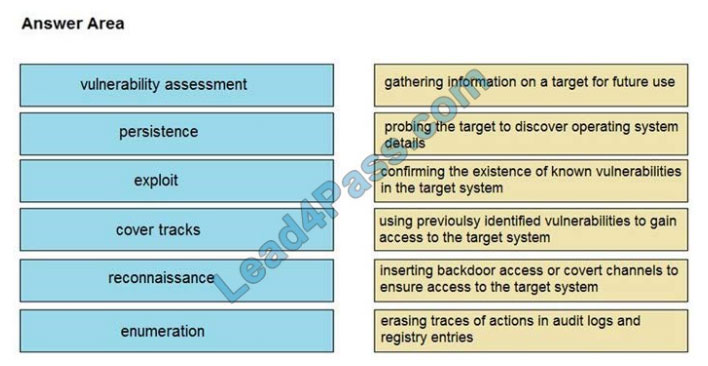
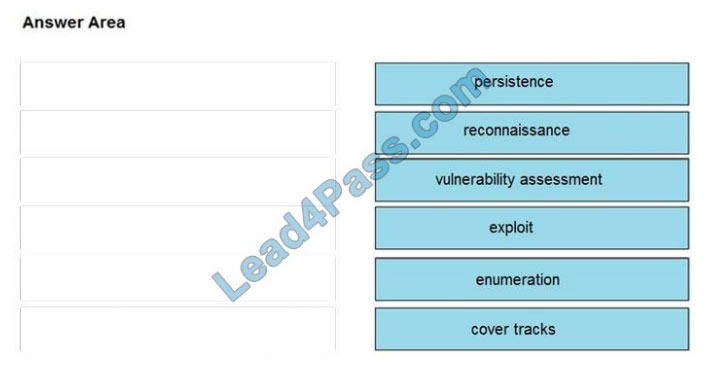
DRAG-DROP
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during
the phases on the right.
Select and Place:
Correct Answer:
QUESTION 4
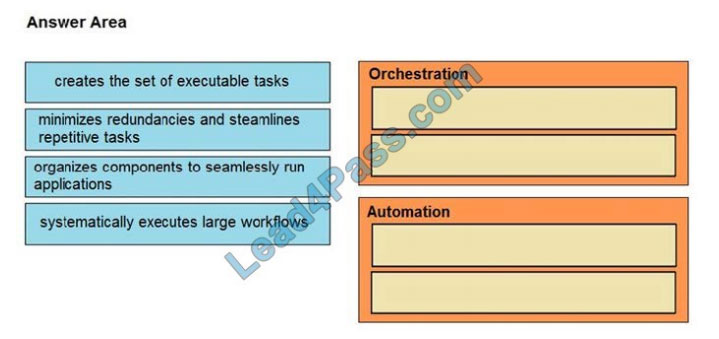
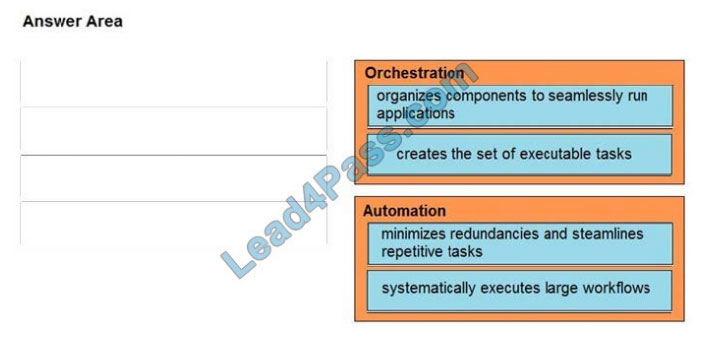
DRAG-DROP
Drag and drop the function on the left onto the mechanism on the right.
Select and Place:
Correct Answer:
QUESTION 5
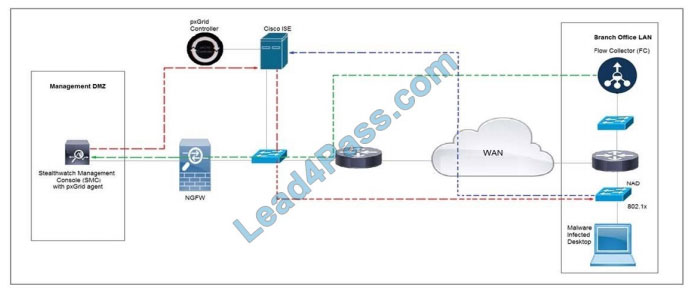
Refer to the exhibit. Cisco Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE
detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a Quarantine VLAN
using Adaptive Network Control policy.
Which telemetry feeds were correlated with SMC to identify the malware?
A. NetFlow and event data
B. event data and Syslog data
C. SNMP and Syslog data
D. NetFlow and SNMP
Correct Answer: B
QUESTION 6
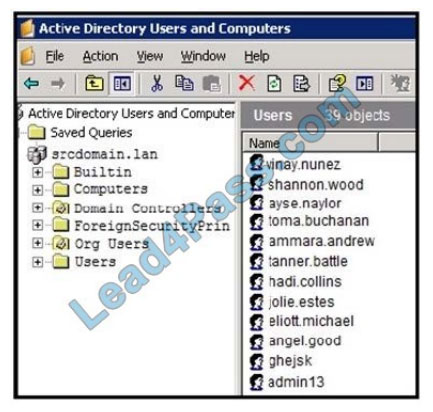
Refer to the exhibit. An engineer is investigating a case with suspicious usernames within the active directory. After the
engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and
their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior.
Which type of compromise is occurring?
A. compromised insider
B. compromised root access
C. compromised database tables
D. compromised network
Correct Answer: D
QUESTION 7
A threat actor used a phishing email to deliver a file with an embedded macro. The file was opened, and a remote code
execution attack occurred in a company\\’s infrastructure. Which steps should an engineer take at the recovery stage?
A. Determine the systems involved and deploy available patches
B. Analyze event logs and restrict network access
C. Review access lists and require users to increase password complexity
D. Identify the attack vector and update the IDS signature list
Correct Answer: B
QUESTION 8
An engineer wants to review the packet overviews of SNORT alerts. When printing the SNORT alerts, all the packet
headers are included, and the file is too large to utilize. Which action is needed to correct this problem?
A. Modify the alert rule to “output alert_syslog: output log”
B. Modify the output module rule to “output alert_quick: output filename”
C. Modify the alert rule to “output alert_syslog: output header”
D. Modify the output module rule to “output alert_fast: output filename”
Correct Answer: A
Reference: https://snort-org-site.s3.amazonaws.com/production/document_files/files/000/000/249/original/snort_manual.
pdf?X-Amz-Algorithm=AWS4-HMAC-SHA256andX-Amz-Credential=AKIAIXACIED2SPMSC7GA%2F20201231%2Fuse
ast-1%2Fs3%2Faws4_requestandX-Amz-Date=20201231T141156ZandX-Amz-Expires=172800andX-Amz-SignedHead
ers=hostandX-Amz-Signature=e122ab6eb1659e13b3bc6bb2451ce693c0298b76c1962c3743924bc5fd83d382
QUESTION 9
An engineer returned to work and realized that payments that were received over the weekend were sent to the wrong
recipient. The engineer discovered that the SaaS tool that processes these payments was down over the weekend.
Which step should the engineer take first?
A. Utilize the SaaS tool team to gather more information on the potential breach
B. Contact the incident response team to inform them of a potential breach
C. Organize a meeting to discuss the services that may be affected
D. Request that the purchasing department creates and sends the payments manually
Correct Answer: A
QUESTION 10
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the
resource?
A. chmod 666
B. chmod 774
C. chmod 775
D. chmod 777
Correct Answer: D
Reference: https://www.pluralsight.com/blog/it-ops/linux-file-permissions
QUESTION 11
Refer to the exhibit. A security analyst needs to investigate a security incident involving several suspicious connections
with a possible attacker. Which tool should the analyst use to identify the source IP of the offender?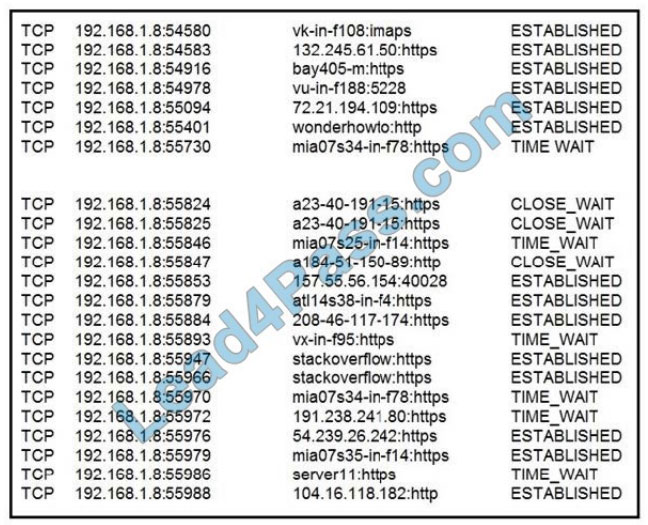
A. packet sniffer
B. malware analysis
C. SIEM
D. firewall manager
Correct Answer: A
QUESTION 12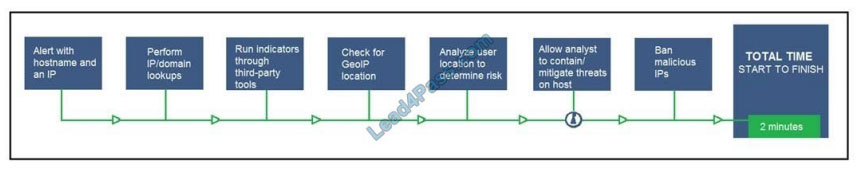
Refer to the exhibit. An engineer configured this SOAR solution workflow to identify account theft threats and privilege
escalation, evaluate risk, and respond by resolving the threat. This solution is handling more threats than Security
analysts have time to analyze. Without this analysis, the team cannot be proactive and anticipate attacks.
Which action will accomplish this goal?
A. Exclude the step “BAN malicious IP” to allow analysts to conduct and track the remediation
B. Include a step “Take a Snapshot” to capture the endpoint state to contain the threat for analysis
C. Exclude the step “Check for GeoIP location” to allow analysts to analyze the location and the associated risk-based
on asset criticality
D. Include a step “Reporting” to alert the security department of threats identified by the SOAR reporting engine
Correct Answer: A
QUESTION 13
DRAG-DROP
Drag and drop the NIST incident response process steps from the left onto the actions that occur in the steps on the
right.
Select and Place: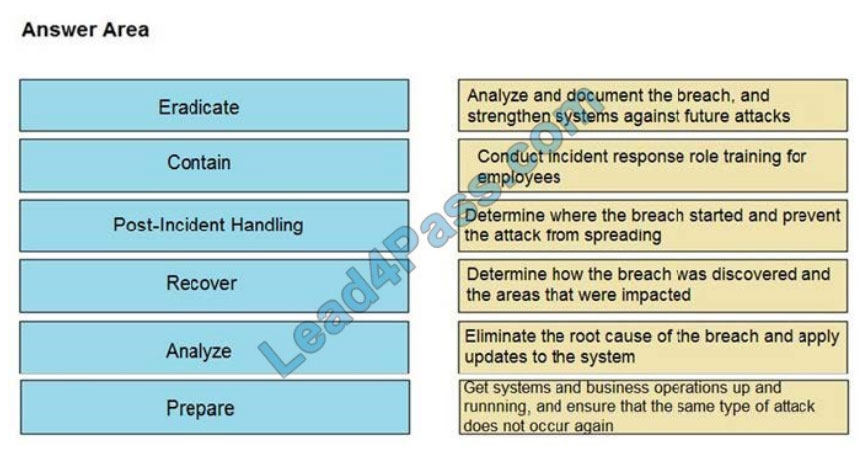
Correct Answer:
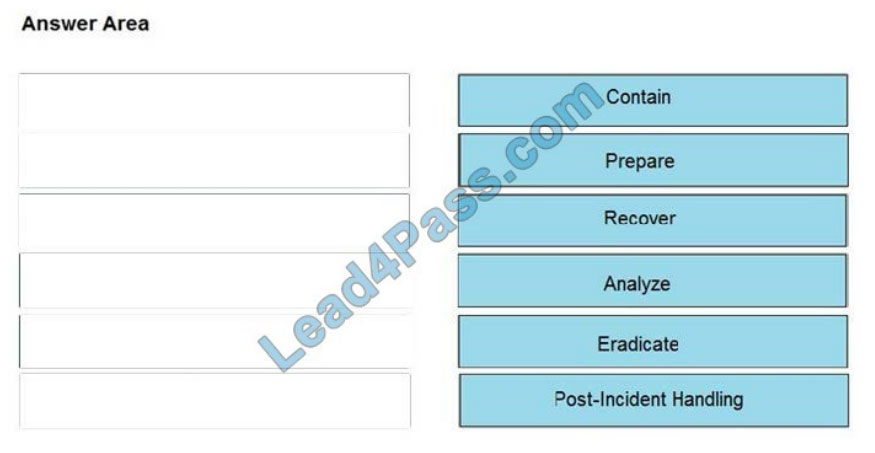
Reference: https://www.securitymetrics.com/blog/6-phases-incident-response-plan
Get the latest and complete Cisco CyberOps Professional 350-201 exam dumps! Help you pass the first exam successfully! Click here for more…
Cisco CyberOps Professional 350-201 Exam Certification Coupon Code 2021
You have read my entire article, and I have already told you how to successfully pass the Cisco CyberOps Professional 350-201 exam. You can choose: https://www.leads4pass.com/350-201.html and go directly to 350-201 Exam dumps channel! Get your key to successfully pass the exam!
Wish you be happy!
ps.
Get free Cisco 350-201 dumps PDF online: https://drive.google.com/file/d/1s19V_3m7G1cpfnNm5DTJ02_zUW1j34Mw/

Recent Comments