
The latest Cisco CCNA Security 640-554 exam dump and 640-554 pdf free sharing, easily pass the Cisco CCNA Security 640-554 exam certification. “Implementing Cisco IOS Network Security (IINS v2.0)” leads4pass.com
year-round exam questions to ensure high pass rates
Table of Contents:
- Latest Cisco CCNA Security 640-554 pdf
- Test your Cisco CCNA Security 640-554 exam level
- Watch the Cisco CCNA Security 640-554 video tutorial online
- Related 640-554 Popular Exam resources
- Get leads4pass Coupons (12% OFF)
- What are the advantages of leads4pass?
Latest Cisco CCNA Security 640-554 pdf
[PDF] Free Cisco CCNA Security 640-554 pdf dumps download from Google Drive: https://drive.google.com/open?id=1J5Vi4WC8i8JqSToidGXobA19AujtT-CG
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
Cisco has decided to retire the 640-554 exam: https://learningnetwork.cisco.com/thread/87198
Test your Cisco CCNA Security 640-554 exam level
QUESTION 1
How many crypto map sets can you apply to a router interface?
A. 3
B. 2
C. 4
D. 1
Correct Answer: D
Crypto Map Guidelines You can apply only one crypto map set to a single interface. The crypto map set can include a
combination of IPsec/IKE and IPsec/manual entries. Multiple interfaces can share the same crypto map set if you want
to apply the same policy to multiple interfaces. Reference: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnips/configuration/xe-3s/asr1000/sec-sec-for-vpns-w-ipsec-xe-3s-asr1000-book/sec-cfg-vpn-ipsec.html
QUESTION 2
What will be disabled as a result of the no service password-recovery command?
A. changes to the config-register setting
B. ROMMON
C. password encryption service
D. aaa new-model global configuration command
E. the xmodem privilege EXEC mode command to recover the Cisco IOS image
Correct Answer: B
Background
ROMMON security is designed not to allow a person with physical access to the router view the configuration file.
ROMMON security disables access to the ROMMON, so that a person cannot set the configuration register to ignore
the startup configuration. ROMMON security is enabled when the router is configured with the no service password-
recovery command.
Caution: Because password recovery that uses ROMMON security destroys the configuration, it is recommended that
you save the router configuration somewhere off the router, such as on a TFTP server.
Risks
If a router is configured with the no service password-recovery command, this disables all access to the ROMMON. If
there is no valid Cisco IOS software image in the Flash memory of the router, the user is not able to use the ROMMON
XMODEM command in order to load a new Flash image. In order to fix the router, you must get a new Cisco IOS
software image on a Flash SIMM, or on a PCMCIA card, for example on the 3600 Series Routers. In order to minimize
this risk,
a customer who uses ROMMON security must also use dual Flash bank memory and put a backup Cisco IOS software
image in a separate partition.
QUESTION 3
Refer to the exhibit.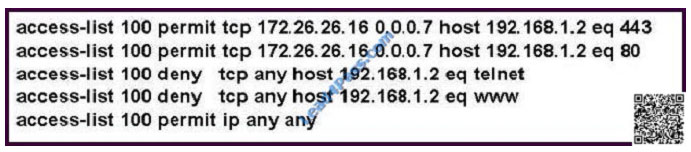
Which traffic is permitted by this ACL?
A. TCP traffic sourced from any host in the 172.26.26.8/29 subnet on any port to host 192.168.1.2 port 80 or 443
B. TCP traffic sourced from host 172.26.26.21 on port 80 or 443 to host 192.168.1.2 on any port
C. any TCP traffic sourced from host 172.26.26.30 destined to host 192.168.1.1
D. any TCP traffic sourced from host 172.26.26.20 to host 192.168.1.2
Correct Answer: C
www.cisco.com/en/US/products/sw/secursw/ps1018/products_tech_note09186a00800a5b9a.shtml
Extended ACLs
Extended ACLs were introduced in Cisco IOS Software Release 8.3. Extended ACLs control traffic by the comparison of
the source and destination addresses of the IP packets to the addresses configured in the ACL.
IP
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} protocol source source-wildcard
destination destination-wildcard [precedence precedence]
[tos tos] [log|log-input] [time-range time-range-name]
ICMP
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} icmp source source-wildcard
destination destination-wildcard
[icmp-type [icmp-code] |icmp-message]
[precedence precedence] [tos tos] [log|log-input]
[time-range time-range-name]
TCP
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} tcp source source-wildcard [operator [port]]
destination destination-wildcard [operator [port]]
[established] [precedence precedence] [tos tos]
[log|log-input] [time-range time-range-name]
UDP
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} udp source source-wildcard [operator [port]]
destination destination-wildcard [operator [port]]
[precedence precedence] [tos tos] [log|log-input]
[time-range time-range-name]
QUESTION 4
Which protocol secures router management session traffic?
A. SSTP
B. POP
C. Telnet
D. SSH
Correct Answer: D
http://www.cisco.com/en/US/tech/tk648/tk361/technologies_tech_note09186a0080120f48.shtml
Encrypting Management Sessions
Because information can be disclosed during an interactive management session, this traffic must be encrypted so that
a malicious user cannot gain access to the data being transmitted. Encrypting the traffic allows a secure remote access
connection to the device. If the traffic for a management session is sent over the network in cleartext, an attacker can
obtain sensitive information about the device and the network. An administrator is able to establish an encrypted and
secure remote access management connection to a device by using the SSH or HTTPS (Secure Hypertext Transfer
Protocol) features. Cisco IOS software supports SSH version 1.0 (SSHv1), SSH version 2.0 (SSHv2), and HTTPS that
uses Secure Sockets Layer (SSL) and Transport Layer Security (TLS) for authentication and data encryption. Note that
SSHv1 and SSHv2 are not compatible.
Cisco IOS software also supports the Secure Copy Protocol (SCP), which allows an encrypted and secure connection
for copying device configurations or software images. SCP relies on SSH. This example configuration enables SSH on a
Cisco IOS device: ! ip domain-name example.com ! crypto key generate rsa modulus 2048 ! ip ssh time-out 60 ip ssh
authentication-retries 3 ip ssh source-interface GigabitEthernet 0/1 ! line vty 0 4 transport input ssh !
QUESTION 5
Which option is a key difference between Cisco IOS interface ACL configurations and Cisco ASA appliance interface
ACL configurations?
A. The Cisco IOS interface ACL has an implicit permit-all rule at the end of each interface ACL.
B. Cisco IOS supports interface ACL and also global ACL. Global ACL is applied to all interfaces.
C. The Cisco ASA appliance interface ACL configurations use netmasks instead of wildcard masks.
D. The Cisco ASA appliance interface ACL also applies to traffic directed to the IP addresses of the Cisco ASA
appliance interfaces.
E. The Cisco ASA appliance does not support standard ACL. The Cisco ASA appliance only support extended ACL.
Correct Answer: C
http://www.cisco.com/en/US/docs/security/asa/asa82/configuration/guide/acl_extended.html Additional Guidelines and
Limitations The following guidelines and limitations apply to creating an extended access list:
•
When you enter the access-list command for a given access list name, the ACE is added to the end of the access list
unless you specify the line number.
•
Enter the access list name in uppercase letters so that the name is easy to see in the configuration. You might want to
name the access list for the interface (for example, INSIDE), or you can name it for the purpose for which it is created
(for example, NO_NAT or VPN).
•
Typically, you identify the ip keyword for the protocol, but other protocols are accepted. For a list of protocol names, see
the “Protocols and Applications” section.
•
Enter the host keyword before the IP address to specify a single address. In this case, do not enter a mask. Enter the
any keyword instead of the address and mask to specify any address.
•
You can specify the source and destination ports only for the tcp or udp protocols. For a list of permitted keywords and
well-known port assignments, see the “TCP and UDP Ports” section. DNS, Discard, Echo, Ident, NTP, RPC, SUNRPC,
and Talk each require one definition for TCP and one for UDP. TACACS+ requires one definition for port 49 on TCP.
•
You can specify the ICMP type only for the icmp protocol. Because ICMP is a connectionless protocol, you either need
access lists to allow ICMP in both directions (by applying access lists to the source and destination interfaces), or you
need to enable the ICMP inspection engine. (See the “Adding an ICMP Type Object Group” section.) The ICMP
inspection engine treats ICMP sessions as stateful connections. To control ping, specify echo-reply (0) (ASA to host) or
echo (8) (host to ASA). See the “Adding an ICMP Type Object Group” section for a list of ICMP types.
•
When you specify a network mask, the method is different from the Cisco IOS software access-list command. The ASA
uses a network mask (for example, 255.255.255.0 for a Class C mask). The Cisco IOS mask uses wildcard bits (for
example, 0.0.0.255).
•
To make an ACE inactive, use the inactive keyword. To reenable it, enter the entire ACE without the inactive keyword.
This feature enables you to keep a record of an inactive ACE in your configuration to make reenabling easier.
•
Use the disable option to disable logging for a specified ACE.
QUESTION 6
Which statement about rule-based policies in Cisco Security Manager is true?
A. Rule-based policies contain one or more rules that are related to a device\\’s security and operations parameters.
B. Rule-based policies contain one or more rules that control how traffic is filtered and inspected on a device.
C. Rule-based policies contain one or more user roles that are related to a device\\’s security and operations
parameters.
D. Rule-based policies contain one or more user roles that control how user traffic is filtered and inspected on a device.
Correct Answer: B
QUESTION 7
Which command will configure AAA accounting using the list of all RADIUS servers on a device to generate a reload
event message when the device reloads?
A. aaa accounting network default start-stop group radius
B. aaa accounting auth-proxy default start-stop group radius
C. aaa accounting system default start-stop group radius
D. aaa accounting exec default start-stop group radius
Correct Answer: C
QUESTION 8
Which statement describes a result of securing the Cisco IOS image using the Cisco IOS image resilience feature?
A. The show version command does not show the Cisco IOS image file location.
B. The Cisco IOS image file is not visible in the output from the show flash command.
C. When the router boots up, the Cisco IOS image is loaded from a secured FTP location.
D. The running Cisco IOS image is encrypted and then automatically backed up to the NVRAM.
E. The running Cisco IOS image is encrypted and then automatically backed up to a TFTP server.
Correct Answer: B
http://www.cisco.com/en/US/docs/ios/security/command/reference/sec_book.html
secure boot-config To take a snapshot of the router running configuration and securely archive it in persistent storage,
use the secure boot-config command in global configuration mode. To remove the secure configuration archive and
disable configuration resilience, use the no form of this command.
secure boot-config [restore filename] no secure boot-config Usage Guidelines Without any parameters, this command
takes a snapshot of the router running configuration and securely archives it in persistent storage. Like the image, the
configuration archive is hidden and cannot be viewed or removed directly from the command-line interface (CLI) prompt
. It is recommended that you run this command after the router has been fully configured to reach a steady state of
operation and the running configuration is considered complete for a restoration, if required. A syslog message is
printed on the console notifying the user of configuration resilience activation. The secure archive uses the time of
creation as its filename. For example, .runcfg-20020616-081702.ar was created July 16 2002 at
8:17:02.
The restore option reproduces a copy of the secure configuration archive as the supplied filename
(disk0:running-config, slot1:runcfg, and so on). The restore operation will work only if configuration resilience is enabled.
The number of restored copies that can be created is unlimited.
The no form of this command removes the secure configuration archive and disables configuration resilience.
An enable, disable, enable sequence has the effect of upgrading the configuration archive if any changes were made to
the running configuration since the last time the feature was disabled.
The configuration upgrade scenario is similar to an image upgrade. The feature detects a different version of Cisco IOS
and notifies the user of a version mismatch. The same command can be run to upgrade the configuration archive to a
newer version after new configuration commands corresponding to features in the new image have been issued.
The correct sequence of steps to upgrade the configuration archive after an image upgrade is as follows:
•
Configure new commands
•
Issue the secure boot-config command secure boot-image To enable Cisco IOS image resilience, use the secure boot-
image command in global configuration mode. To disable Cisco IOS image resilience and release the secured image so
that it can be safely removed, use the no form of this command.
secure boot-image no secure boot-image Usage Guidelines This command enables or disables the securing of the
running Cisco IOS image. The following two possible scenarios exist with this command.
•
When turned on for the first time, the running image (as displayed in the show version command output) is secured, and
a syslog entry is generated. This command will function properly only when the system is configured to run an image
from a disk with an Advanced Technology Attachment (ATA) interface. Images booted from a TFTP server cannot be
secured. Because this command has the effect of “hiding” the running image, the image file will not be included in any
directory listing of the disk. The no form of this command releases the image so that it can be safely removed.
•
If the router is configured to boot up with Cisco IOS resilience and an image with a different version of Cisco IOS is
detected, a message similar to the following is displayed at bootup:
ios resilience :Archived image and configuration version 12.2 differs from running version 12.3.
Run secure boot-config and image commands to upgrade archives to running version.
To upgrade the image archive to the new running image, reenter this command from the console. A message will be
displayed about the upgraded image. The old image is released and will be visible in the dir command output.
QUESTION 9
Which alert protocol is used with Cisco IPS Manager Express to support up to 10 sensors?
A. SDEE
B. Syslog
C. SNMP
D. CSM
Correct Answer: A
QUESTION 10
How can the administrator enable permanent client installation in a Cisco AnyConnect VPN firewall configuration?
A. Issue the command anyconnect keep-installer under the group policy or username webvpn mode
B. Issue the command anyconnect keep-installer installed in the global configuration
C. Issue the command anyconnect keep-installer installed under the group policy or username webvpn mode
D. Issue the command anyconnect keep-installer installer under the group policy or username webvpn mode
Correct Answer: D
To enable permanent client installation for a specific group or user, use the anyconnect keep-installer command from
group-policy or username webvpn modes: anyconnect keep-installer installer The default is that permanent installation
of the client is enabled. The client remains on the remote computer at the end of the session. The following example
configures the existing group-policy sales to remove the client on the remote computer at the end of the session:
hostname(config)# group-policy sales attributes hostname(config-group-policy)# webvpn hostname(config-group-
policy)# anyconnect keep-installer installed none
Reference: http://www.cisco.com/c/en/us/td/docs/security/asa/asa84/configuration/guide/asa_84_cli_config/vpn_anyconnect.html
QUESTION 11
Which two services are provided by IPsec? (Choose two.)
A. Confidentiality
B. Encapsulating Security Payload
C. Data Integrity
D. Authentication Header
E. Internet Key Exchange
Correct Answer: AC
http://www.cisco.com/en/US/docs/net_mgmt/vpn_solutions_center/2.0/ip_security/provisioning/guide/IPsecPG1.html
IPsec Overview A secure network starts with a strong security policy that defines the freedom of access to information
and dictates the deployment of security in the network. Cisco Systems offers many technology solutions for building a
custom security solution for Internet, extranet, intranet, and remote access networks. These scalable solutions
seamlessly interoperate to deploy enterprise-wide network security. Cisco System\\’s IPsec delivers a key technology
component for providing a total security solution. Cisco\\’s IPsec offering provides privacy, integrity, and authenticity for
transmitting sensitive information over the Internet.
Cisco\\’s end-to-end offering allows customers to implement IPsec transparently into the network infrastructure without
affecting individual workstations or PCs. Cisco IPsec technology is available across the entire range of computing
infrastructurE. Windows 95, Windows NT 4.0, and Cisco IOS software.
IPsec is a framework of open standards for ensuring secure private communications over the Internet. Based on
standards developed by the Internet Engineering Task Force (IETF), IPsec ensures confidentiality, integrity, and
authenticity of data communications across a public network. IPsec provides a necessary component of a standards-
based, flexible solution for deploying a network-wide security policy.
QUESTION 12
Which AAA feature can automate record keeping within a network?
A. TACACS+
B. authentication
C. authorization
D. accounting
Correct Answer: D
In AAA, accounting refers to the record-keeping and tracking of user activities on a computer network. For a given time
period this may include, but is not limited to, real-time accounting of time spent accessing the network, the network
services employed or accessed, capacity and trend analysis, network cost allocations, billing data, login data for user
authentication and authorization, and the data or data amount accessed or transferred. Reference: http://www.techopedia.com/definition/24130/authentication-authorization-and-accounting-aaa
QUESTION 13
Refer to the exhibit.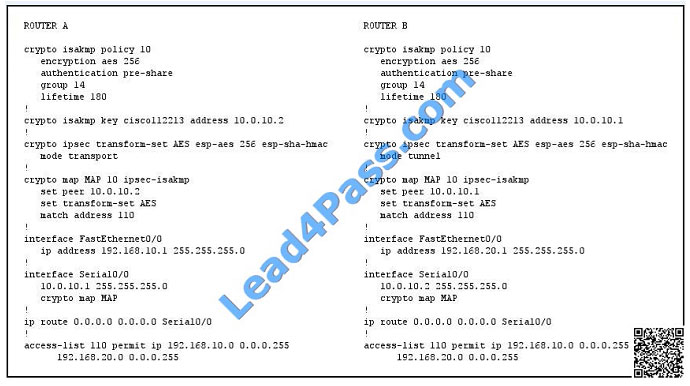
Which two changes must you make to the given IOS site-to-site VPN configuration to enable the routers to form a
connection? (Choose two.)
A. Configure a valid route on Router A.
B. Configure the access list on Router B to mirror Router A.
C. Configure Router B\\’s ISAKMP policy to match the policy on Router A.
D. Configure the tunnel modes on the two routers to match.
Correct Answer: BD
You must configure symmetric crypto ACLs for use by IPsec. Both inbound and outbound traffic are evaluated against
the same outbound IPsec ACL. The ACL criteria are applied in the forward direction to traffic exiting your router, and the
reverse direction to traffic entering your router. When a router receives encrypted packets back from an IPsec peer, it
uses the same ACL to determine which inbound packets to decrypt by viewing the source and destination addresses in
the ACL in reverse order. Note Important: The crypto ACLs used by IPsec must mirror-image ACLs because both
inbound and outbound traffic is evaluated against the same outbound IPsec ACL. Also, the tunnel modes must match
on each end. Here we see that Router A is using
transport mode while Router B is configured for tunnel mode.
Reference: http://lonetsec.blogspot.com/2011/02/cisco-cli-site-to-site-ipsec-vpn.html
QUESTION 14
Which aaa accounting command is used to enable logging of the start and stop records for user terminal sessions on
the router?
A. aaa accounting network start-stop tacacs+
B. aaa accounting system start-stop tacacs+
C. aaa accounting exec start-stop tacacs+
D. aaa accounting connection start-stop tacacs+
E. aaa accounting commands 15 start-stop tacacs+
Correct Answer: C
http://www.cisco.com/en/US/docs/ios/security/command/reference/sec_book.html
aaa accounting To enable authentication, authorization, and accounting (AAA) accounting of requested services for
billing or security purposes when you use RADIUS or TACACS+, use the aaa accounting command in global
configuration mode or template configuration mode. To disable AAA accounting, use the no form of this command. aaa
accounting {auth-proxy | system | network | exec | connection | commands level | dot1x} {default | list-name | guarantee-
first} [vrf vrf-name] {start-stop | stop-only | none} [broadcast] {radius | group group-name} no aaa accounting {authproxy |
system | network | exec | connection | commands level | dot1x} {default | listname | guarantee-first} [vrf vrf-name] {start-
stop | stop-only | none} [broadcast] {radius | group group-name} exec Runs accounting for the EXEC shell session. start-
stop Sends a “start” accounting notice at the beginning of a process and a “stop” accounting notice at the end of a
process. The “start” accounting record is sent in the background. The requested user process begins regardless of
whether the “start” accounting notice was received by the accounting server.
QUESTION 15
Which statement about the role-based CLI access views on a Cisco router is true?
A. The maximum number of configurable CLI access views is 10, including one lawful intercept view and excluding the
root view.
B. The maximum number of configurable CLI access views is 10, including one superview.
C. The maximum number of configurable CLI access views is 15, including one lawful intercept view and excluding the
root view.
D. The maximum number of configurable CLI access views is 15, including one lawful intercept view.
Correct Answer: C
QUESTION 16
Which Cisco Security Manager application collects information about device status and uses it to generate notifications
and alerts?
A. FlexConfig
B. Device Manager
C. Report Manager
D. Health and Performance Monitor
Correct Answer: D
Health and Performance Monitor – Health and Performance Monitor (HPM) periodically polls monitored ASA devices,
IPS devices, and ASA-hosted VPN services for key health and performance data, including critical and non-critical
issues,
such as memory usage, interface status, dropped packets, tunnel status, and so on. This information is used for alert
generation and email notification, and to display trends based on aggregated data, which is available for hourly, daily,
and
weekly periods.
Reference:
http://www.cisco.com/c/en/us/td/docs/security/security_management/cisco_security_manager/security_manager/4-4/user/guide/CSMUserGuide_wrapper/wfplan.html
QUESTION 17
Which type of Cisco ASA access list entry can be configured to match multiple entries in a single statement?
A. nested object-class
B. class-map
C. extended wildcard matching
D. object groups
Correct Answer: D
http://www.cisco.com/en/US/docs/security/asa/asa82/configuration/guide/objectgroups.html
Information About Object Groups
By grouping like objects together, you can use the object group in an ACE instead of having to enter an ACE for each
object separately. You can create the following types of object groups:
•
Protocol
•
Network
•
Service
•
ICMP type
For example, consider the following three object groups:
•
MyServices — Includes the TCP and UDP port numbers of the service requests that are allowed access to the internal
network.
•
TrustedHosts — Includes the host and network addresses allowed access to the greatest range of services and servers.
•
PublicServers — Includes the host addresses of servers to which the greatest access is provided.
After creating these groups, you could use a single ACE to allow trusted hosts to make specific service requests to a
group of public servers.
You can also nest object groups in other object groups.
QUESTION 18
What is the purpose of a trunk port?
A. A trunk port carries traffic for multiple VLANs.
B. A trunk port connects multiple hubs together to increase bandwidth.
C. A trunk port separates VLAN broadcast domains.
D. A trunk port provides a physical link specifically for a VPN.
Correct Answer: A
Ethernet interfaces can be configured either as access ports or trunk ports. Trunks carry the traffic of multiple VLANs
over a single link and allow you to extend VLANs across the network. Reference: http://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus5000/sw/configuration/guide/cli/CLIConfigurationGuide/AccessTrunk.html
QUESTION 19
A Cisco ASA appliance has three interfaces configured. The first interface is the inside interface with a security level of
100. The second interface is the DMZ interface with a security level of 50. The third interface is the outside interface
with a security level of 0.
By default, without any access list configured, which five types of traffic are permitted? (Choose five.)
A. outbound traffic initiated from the inside to the DMZ
B. outbound traffic initiated from the DMZ to the outside
C. outbound traffic initiated from the inside to the outside
D. inbound traffic initiated from the outside to the DMZ
E. inbound traffic initiated from the outside to the inside
F. inbound traffic initiated from the DMZ to the inside
G. HTTP return traffic originating from the inside network and returning via the outside interface
H. HTTP return traffic originating from the inside network and returning via the DMZ interface
I. HTTP return traffic originating from the DMZ network and returning via the inside interface
J. HTTP return traffic originating from the outside network and returning via the inside interface
Correct Answer: ABCGH
QUESTION 20
Which security measures can protect the control plane of a Cisco router? (Choose two.)
A. CCPr
B. Parser views
C. Access control lists
D. Port security
E. CoPP
Correct Answer: AE
Reference: http://www.ciscopress.com/articles/article.asp?p=1924983andseqNum=3
QUESTION 21
Which one of the following items may be added to a password stored in MD5 to make it more secure?
A. Ciphertext
B. Salt
C. Cryptotext
D. Rainbow table
Correct Answer: B
Making an Md5 Hash More Secure To make the md5 hash more secure we need to add what is called “salt”. Salt in this
sense of the meaning is random data appended to the password to make the hash more complicated and difficult to
reverse engineer. Without knowing what the salt is, rainbow table attacks are mostly useless. Reference:
http://www.marksanborn.net/php/creating-a-secure-md5-hash-for-storing-passwords-in-a-database/
QUESTION 22
Which command will block external spoofed addresses?
A. access-list 128 deny ip 10.0.0.0 0.0.255.255 any
B. access-list 128 deny ip 192.168.0.0 0.0.0.255 any
C. access-list 128 deny ip 10.0.0.0 0.255.255.255 any
D. access-list 128 deny ip 192.168.0.0 0.0.31.255 any
Correct Answer: C
QUESTION 23
In an IPsec VPN, what determination does the access list make about VPN traffic?
A. whether the traffic should be blocked
B. whether the traffic should be permitted
C. whether the traffic should be encrypted
D. the peer to which traffic should be sent
Correct Answer: C
Crypto access lists are used to define which IP traffic will be protected by crypto and which traffic will not be protected
by crypto (encrypted). These access lists are not the same as regular access lists, which determine what traffic to
forward or block at an interface. For example, access lists can be created to protect all IP traffic between Subnet A and
Subnet Y or Telnet traffic between Host A and Host B. Reference:
http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfipsec.html#wp1001139
QUESTION 24
What features can protect the data plane? (Choose three.)
A. policing
B. ACLs
C. IPS
D. antispoofing
E. QoS
F. DHCP-snooping
Correct Answer: BDF
Reference: http://www.ciscopress.com/articles/article.asp?p=1924983andseqNum=5
QUESTION 25
Which authentication protocol does the Cisco AnyConnect VPN password management feature require to operate?
A. MS-CHAPv1
B. MS-CHAPv2
C. CHAP
D. Kerberos
Correct Answer: B
QUESTION 26
How are Cisco IOS access control lists processed?
A. Standard ACLs are processed first.
B. The best match ACL is matched first.
C. Permit ACL entries are matched first before the deny ACL entries.
D. ACLs are matched from top down.
E. The global ACL is matched first before the interface ACL.
Correct Answer: D
http://www.cisco.com/en/US/products/sw/secursw/ps1018/products_tech_note09186a00800a5b9a.shtml
Process ACLs Traffic that comes into the router is compared to ACL entries based on the order that the entries occur in
the router. New statements are added to the end of the list. The router continues to look until it has a match. If no
matches are found when the router reaches the end of the list, the traffic is denied. For this reason, you should have the
frequently hit entries at the top of the list. There is an implied deny for traffic that is not permitted. A single-entry ACL
with only one deny entry has the effect of denying all traffic. You must have at least one permit statement in an ACL or
all traffic is blocked. These two ACLs (101 and 102) have the same effect.
QUESTION 27
Refer to the exhibit.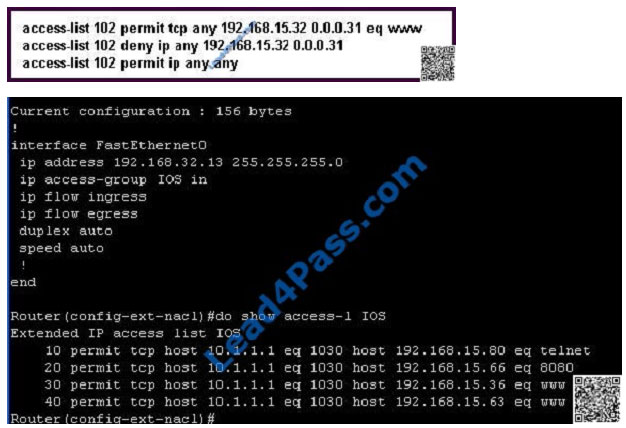
This Cisco IOS access list has been configured on the FA0/0 interface in the inbound direction.
Which four TCP packets sourced from 10.1.1.1 port 1030 and routed to the FA0/0 interface are permitted? (Choose
four.)
A. destination ip address: 192.168.15.37 destination port: 22
B. destination ip address: 192.168.15.80 destination port: 23
C. destination ip address: 192.168.15.66 destination port: 8080
D. destination ip address: 192.168.15.36 destination port: 80
Latest 640-554 Dumps | 640-554 VCE Dumps | 640-554 Study Guide 17 / 27https://www.leads4pass.com/640-554.html
2019 Latest leads4pass 640-554 PDF and VCE dumps Download
E. destination ip address: 192.168.15.63 destination port: 80
F. destination ip address: 192.168.15.40 destination port: 21
Correct Answer: BCDE
http://www.cisco.com/en/US/tech/tk648/tk361/technologies_configuration_example09186a0080100548.shtml
Extended ACLs (registered customers only) control traffic by comparing the source and destination addresses of the IP
packets to the addresses configured in the ACL. You can also make extended ACLs more granular and configured to
filter
traffic by criteria such as:
Protocol
Port numbers
Differentiated services code point (DSCP) value
Precedence value
State of the synchronize sequence number (SYN) bit
The command syntax formats of extended ACLs are:
IP
access-list access-list-number [dynamic dynamic-name [timeout minutes]]
{deny | permit} protocol source source-wildcard destination
destination-wildcard
[precedence precedence] [tos tos] [log | log-input]
[time-range time-range-name][fragments]
Internet Control Message Protocol (ICMP)
access-list access-list-number [dynamic dynamic-name [timeout minutes]]
{deny | permit}
icmp source source-wildcard destination destination-wildcard [icmp-type
[icmp-code] | [icmp-message]] [precedenceprecedence] [tos tos] [log |
log-input] [time-range time-range-name][fragments]
Transport Control Protocol (TCP)
access-list access-list-number [dynamic dynamic-name [timeout minutes]]
{deny | permit} tcp
source source-wildcard [operator [port]] destination destination-wildcard
[operator [port]] [established] [precedence precedence] [tos tos] [log |
log-input] [time-range time-range-name][fragments]
User Datagram Protocol (UDP)
access-list access-list-number [dynamic dynamic-name [timeout minutes]]
{deny | permit} udp
source source-wildcard [operator [port]] destination destination-wildcard
[operator [port]] [precedence precedence] [tos tos] [log | log-input]
[time-range time-range-name][fragments]
QUESTION 28
Which Cisco feature can help mitigate spoofing attacks by verifying symmetry of the traffic path?
A. Unidirectional Link Detection
B. Unicast Reverse Path Forwarding
C. TrustSec
D. IP Source Guard
Correct Answer: B
QUESTION 29
Which network security framework is used to set up access control on Cisco Appliances?
A. RADIUS
B. AAA
C. TACACS+
D. NAS
Correct Answer: B
AAA is a security framework that can be used to set up access control on Cisco routers, switches, firewalls, and other
network appliances. AAA provides the ability to control who is allowed to access network devices and what services the
user should be allowed to access. AAA services are commonly used to control telnet or console access to network
devices.
Reference: http://www.freeccnastudyguide.com/study-guides/ccna/ch8/aaa-security/
QUESTION 30
When AAA login authentication is configured on Cisco routers, which two authentication methods should be used as the
final method to ensure that the administrator can still log in to the router in case the external AAA server fails? (Choose
two.)
A. group RADIUS
B. group TACACS+
C. local
D. krb5
E. enable
F. if-authenticated
Correct Answer: CE
http://www.cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scftplus.html
TACACS+ Authentication Examples The following example shows how to configure TACACS+ as the security protocol
for PPP authentication: aaa new-model aaa authentication ppp test group tacacs+ local tacacs-server host 10.1.2.3
tacacs-server key goaway interface serial 0 ppp authentication chap pap test The lines in the preceding sample
configuration are defined as follows:
•
The aaa new-model command enables the AAA security services.
•
The aaa authentication command defines a method list, “test,” to be used on serial interfaces running PPP. The
keyword group tacacs+ means that authentication will be done through TACACS+. If TACACS+ returns an ERROR of
some sort during authentication, the keyword local indicates that authentication will be attempted using the local
database on the network access server.
http://www.cisco.com/en/US/tech/tk59/technologies_tech_note09186a00800946a3.shtml Authentication Start to
configure TAC+ on the router. Enter enable mode and type configure terminal before the command set. This command
syntax ensures that you are not locked out of the router initially, providing the tac_plus_executable is not running: !—
Turn on TAC+. aaa new-model enable password whatever !— These are lists of authentication methods. !—
“linmethod”, “vtymethod”, “conmethod”, and !— so on are names of lists, and the methods !— listed on the same lines
are the methods !— in the order to be tried. As used here, if !— authentication fails due to the !— tac_plus_executable
not being started, the !— enable password is accepted because !— it is in each list. ! aaa authentication login linmethod
tacacs+ enable aaa authentication login vtymethod tacacs+ enable aaa authentication login conmethod tacacs+ enable
QUESTION 31
Which command provides phase 1 and phase 2 status for all active sessions of an IPsec VPN on a Cisco router?
A. show crypto map
B. show crypto ipsec sa
C. show crypto isakmp sa
D. show crypto session
Correct Answer: D
QUESTION 32
Which option describes information that must be considered when you apply an access list to a physical interface?
A. Protocol used for filtering
B. Direction of the access class
C. Direction of the access group
D. Direction of the access list
Correct Answer: C
QUESTION 33
On which Cisco Configuration Professional screen do you enable AAA?
A. AAA Summary
B. AAA Servers and Groups
C. Authentication Policies
D. Authorization Policies
Correct Answer: A
Authentication/Authorization: These fields are visible when AAA is enabled on the router. AAA can be enabled by
clicking Configure > Router > AAA > AAA Summary > Enable AAA.
Reference: Cisco Configuration Professional User Guide 2.5 PDF
QUESTION 34
Which two protocols are used in a server-based AAA deployment? (Choose two.)
A. RADIUS
B. TACACS+
C. HTTPS
D. WCCP E. HTTP
Correct Answer: AB
Remote Security Database Standards Supported by Cisco Several remote security database standards have been
written to provide uniform access control for network equipment and users. A variety of applications have been
developed as shareware and as commercial products to conform to the standards. Cisco network equipment supports
the three primary security server protocols: TACACS+, RADIUS, and Kerberos. TACACS+ and RADIUS are the
predominant security server protocols used for AAA with network access servers, routers, and firewalls. These protocols
are used to communicate access control information between the security server and the network equipment. Cisco has
also developed the CiscoSecure ACS family of remote security databases to support the TACACS+ and RADIUS
protocols. Reference: http://www.ciscopress.com/articles/article.asp?p=25471andseqNum=6
QUESTION 35
Which statement describes how VPN traffic is encrypted to provide confidentiality when using asymmetric encryption?
A. The sender encrypts the data using the sender\\’s private key, and the receiver decrypts the data using the sender\\’s
public key.
B. The sender encrypts the data using the sender\\’s public key, and the receiver decrypts the data using the sender\\’s
private key.
C. The sender encrypts the data using the sender\\’s public key, and the receiver decrypts the data using the receiver\\’s
public key.
D. The sender encrypts the data using the receiver\\’s private key, and the receiver decrypts the data using the
receiver\\’s public key.
E. The sender encrypts the data using the receiver\\’s public key, and the receiver decrypts the data using the
receiver\\’s private key.
F. The sender encrypts the data using the receiver\\’s private key, and the receiver decrypts the data using the
sender\\’s public key.
Correct Answer: E
http://www.cisco.com/en/US/tech/tk1132/technologies_white_paper09186a00800e79cb.shtml
Public-Key Cryptography and Asymmetric Encryption
In asymmetric encryption, two different keys are used to render data illegible to anyone who may be eavesdropping on a
conversation. The certificates contain the two components of asymmetric encryption:
public key and private key.
Data that is encrypted with the public key can be decrypted with the private key, and vice versa. However, data
encrypted with the public key cannot be decrypted with the public key. The parties who need to encrypt their
communications will
exchange their public keys (contained in the certificate), but will not disclose their private keys. The sending party will
use the public key of the receiving party to encrypt message data and forward the ciphertext (encrypted data) to the
other
party. The receiving party will then decrypt the ciphertext with their private key.
Data encrypted with the public key cannot be decrypted with the public key. This prevents someone from compromising
the ciphertext after acquiring both public keys by eavesdropping on the certificate exchange.
QUESTION 36
Which command verifies phase 2 of an IPsec VPN on a Cisco router?
A. show crypto map
B. show crypto ipsec sa
C. show crypto isakmp sa
D. show crypto engine connection active
Correct Answer: B
show crypto isakmp sa [active | standby] Shows the ISAKMP/IKE Phase 1 management SAs; you can qualify the
command with two parameters, where active displays only the active SAs and standby displays only the SAs in an
“STDBY” (standby) state. show crypto ipsec sa [active | standby] Shows the ISAKMP/IKE Phase 2 data SAs; you can
qualify this command with two parameters, which perform the same function as described in the last bullet point.
Reference: https://sites.google.com/site/networkexams/tccnp-icsw1
QUESTION 37
When port security is enabled on a Cisco Catalyst switch, what is the default action when the configured maximum
number of allowed MAC addresses value is exceeded?
A. The port remains enabled, but bandwidth is throttled until old MAC addresses are aged out.
B. The port is shut down.
C. The MAC address table is cleared and the new MAC address is entered into the table.
D. The violation mode of the port is set to restrict.
Correct Answer: B
http://www.cisco.com/en/US/docs/switches/lan/catalyst4500/12.2/20ewa/configuration/guide/port_sec.html
Default Port Security Configuration Port security Disabled on a port Maximum number of secure MAC addresses
Violation mode Shutdown. The port shuts down when the maximum number of secure MAC addresses is exceeded,
and an SNMP trap notification is sent.
Aging Disabled
Aging type Absolute Static Aging Disabled
Sticky Disabled
QUESTION 38
Refer to the exhibit.
You are a network manager for your organization. You are looking at your Syslog server reports. Based on the Syslog
message shown, which two statements are true? (Choose two.)
A. Service timestamps have been globally enabled.
B. This is a normal system-generated information message and does not require further investigation.
C. This message is unimportant and can be ignored.
D. This message is a level 5 notification message.
Correct Answer: AD
http://www.cisco.com/en/US/docs/switches/lan/catalyst2960/software/release/12.2_55_se/configuration/guide/swlog.html
System Log Message Format
System log messages can contain up to 80 characters and a percent sign (%), which follows the optional sequence
number or time-stamp information, if configured. Messages appear in this format:
seq no:timestamp: %facility-severity-MNEMONIC:description (hostname-n)
The part of the message preceding the percent sign depends on the setting of the service sequence-numbers, service
timestamps log datetime, service timestamps log datetime [localtime] [msec] [show-timezone], or service timestamps
log
uptime global configuration command.
seq no:
Stamps log messages with a sequence number only if the service sequence-numbers global configuration command is
configured. For more information, see the “Enabling and Disabling Sequence Numbers in Log Messages” section.
timestamp formats:
mm/dd hh:mm:ss
or
hh:mm:ss (short uptime)
or
d h (long uptime)
Date and time of the message or event. This information appears only if the service timestamps log [datetime | log]
global configuration command is configured. For more information, see the “Enabling and Disabling Time Stamps on
Log
Messages” section.facility The facility to which the message refers (for example, SNMP, SYS, and so forth). For a list of
supported facilities, see Table 29-4.severity Single-digit code from 0 to 7 that is the severity of the message. For a
description of the severity levels, see Table 29-3.
MNEMONIC
Text string that uniquely describes the message.
description
Text string containing detailed information about the event being reported.
http://www.cisco.com/en/US/docs/switches/lan/catalyst2960/software/release/12.2_55_se/configuration/guide/swlog.htm
l This example shows part of a logging display with the service timestamps log datetime global configuration command
enabled:
*Mar 1 18:46:11: %SYS-5-CONFIG_I: Configured from console by vty2 (10.34.195.36) (Switch-2)
QUESTION 39
Which components does HMAC use to determine the authenticity and integrity of a message? (Choose two.)
A. The password
B. The hash
C. The key
D. The transform set
Correct Answer: BC
Reference: https://supportforums.cisco.com/document/6531/hmac
QUESTION 40
Which statement is true about configuring access control lists to control Telnet traffic destined to the router itself?
A. The ACL is applied to the Telnet port with the ip access-group command.
B. The ACL should be applied to all vty lines in the in direction to prevent an unwanted user from connecting to an
unsecured port.
C. The ACL applied to the vty lines has no in or out option like ACL being applied to an interface.
D. The ACL must be applied to each vty line individually.
Correct Answer: B
http://www.cisco.com/en/US/docs/ios-xml/ios/sec_data_acl/configuration/12-4t/sec-cntrl-acc-vtl.html
Controlling Access to a Virtual Terminal Line
You can control who can access the virtual terminal lines (vtys) to a router by applying an access list to inbound vtys.
You can also control the destinations that the vtys from a router can reach by applying an access list to outbound vtys.
Benefits of Controlling Access to a Virtual Terminal Line
By applying an access list to an inbound vty, you can control who can access the lines to a router. By applying an
access list to an outbound vty, you can control the destinations that the lines from a router can reach.
Related 640-554 Popular Exam resources
| title | youtube | Cisco has decided to retire the 640-554 exam | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| Cisco 640-554 | leads4pass 640-554 dumps pdf | leads4pass 640-554 youtube | Cisco has decided to retire the 640-554 exam | https://www.leads4pass.com/640-554.html | 308 Q&A |
| Cisco CCNA Security | https://www.leads4pass.com/210-260.html | 505 Q&A |
Get leads4pass Coupons(12% OFF)
What are the advantages of leads4pass?
We have a number of cisco, Microsoft, IBM, CompTIA, and other exam experts. We update exam data throughout the year.
Top exam pass rate! We have a large user base. We are an industry leader! Choose leads4pass to pass the exam with ease!
Summarize:
We collect the latest Cisco CCNA Security 640-554 exam questions and answers as part of the first step to help you pass the exam.
You can download 640-554 pdf online or watch youtube. Here you can improve your skills and exam experience! Click here for the full 640-554 exam questions.
Discover more from Provide the most popular Cisco (CCNA, CCNP, CCIE, CCDP...) IT certification exam questions and answers, exam dumps, Leads4pass expert team will help you easily obtain Cisco, Microsoft, CompTIA, Citrix, Amazon IT certification
Subscribe to get the latest posts sent to your email.

Recent Comments