
If you’re planning to take the Cisco 350-201 CBRCOR exam, a preparation strategy is crucial.
The cybersecurity landscape is changing fast, and Cisco has adjusted its CyberOps Professional track to better match today’s real-world SOC environments. As attacks become more automated and complex, certifications that demonstrate deep analysis skills—like 350-201 CBRCOR—have become significantly more valuable for career growth.
In this guide, you’ll learn why updated 350-201 dumps remain one of the most effective ways to prepare, where to access trusted resources, and what recent changes you need to know before sitting for the exam.
What Is the Cisco 350-201 CBRCOR Exam?
The 350-201 exam, officially named Performing CyberOps Using Cisco Security Technologies, is the core requirement in the Cisco Certified CyberOps Professional path. It validates your capability to detect, analyze, and respond to cybersecurity incidents using Cisco-powered security solutions.
As of December 2025, the exam still includes:
- 90–110 questions
- 120-minute duration
- English-only delivery
- $400 USD exam fee
Its focus remains hands-on and scenario-driven, emphasizing detection tools, secure network analytics, forensic investigation, and advanced incident response.
Latest 2025 Cisco Updates You Should Know
Cisco updated several components of the CyberOps Professional portfolio in late 2024 and again in mid-2025. These updates continue into the 2026 exam cycle. Key shifts include:
- More emphasis on AI-assisted threat identification
- Expanded coverage of cloud-native incident response
- Updated analytics for encrypted traffic visibility
- Higher difficulty in interpreting multi-stage attack chains
These changes make it essential to rely on 2025-updated exam materials, as older resources do not reflect the revised blueprint.
Why Using Updated 350-201 Dumps Improves Exam Success
The 350-201 exam is known for detailed scenarios that require analytical thinking rather than memorization. Updated dumps allow you to:
- Experience question structures identical to the live exam
- Review hard-to-interpret threat-analysis items
- Improve confidence by practicing hands-on-style reasoning
- Focus on the blueprint areas that Cisco recently strengthened
In 2025–2026, dumps remain one of the fastest ways to train your brain for complex decision-making under time pressure.
What You Get with the Latest 350-201 Dumps (PDF + VCE)
The newest dumps include:
- PDF + VCE formats, suitable for mobile and desktop learning
- 365-day free updates, ensuring year-round accuracy
- Detailed explanations for challenging questions, not just answers
- Support from a professional Cisco technical team
- Full coverage of all CBRCOR domains
For trusted resources, the most reliable provider used by many candidates remains Leads4Pass 350-201 Dumps (https://www.leads4pass.com/350-201.html).
Sharing the latest Cisco 350-201 exam questions and answers
This is currently the latest free learning material for the Cisco 350-201 available online.
| Number of exam questions | Complete study materials |
| 15 (Free) | 139 Q&A |
Question 1:
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their organization monitors. The email includes a suspicious attachment titled “Invoice RE: 0004489”. The hash of the file is gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this hash is found anywhere on the web.
What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?
A. Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B. Ask the company to execute the payload for real time analysis
C. Investigate further in open source repositories using YARA to find matches
D. Obtain a copy of the file for detonation in a sandbox
Correct Answer: D
Question 2:
A security expert is investigating a breach that resulted in a $32 million loss from customer accounts. Hackers were able to steal API keys and two-factor codes due to a vulnerability that was introduced in a new code a few weeks before the attack.
Which step was missed that would have prevented this breach?
A. use of the Nmap tool to identify the vulnerability when the new code was deployed
B. implementation of a firewall and intrusion detection system
C. implementation of an endpoint protection system
D. use of SecDevOps to detect the vulnerability during development
Correct Answer: D
Reference: https://securityintelligence.com/how-to-prioritize-security-vulnerabilities-in-secdevops/
Question 3:
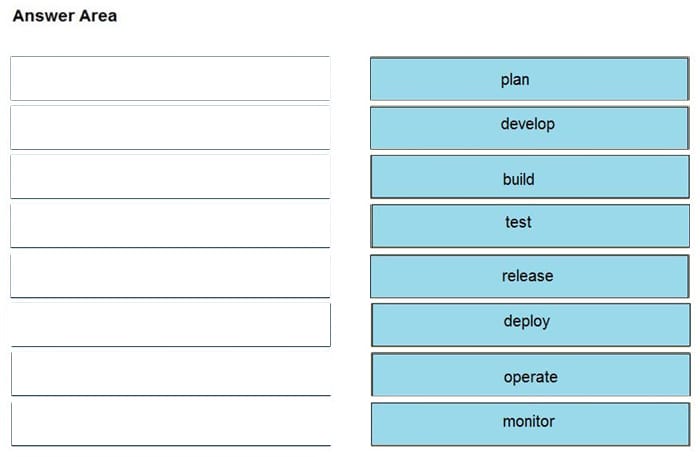
DRAG DROP
Drag and drop the components from the left onto the phases of the CI/CD pipeline on the right.
Select and Place:
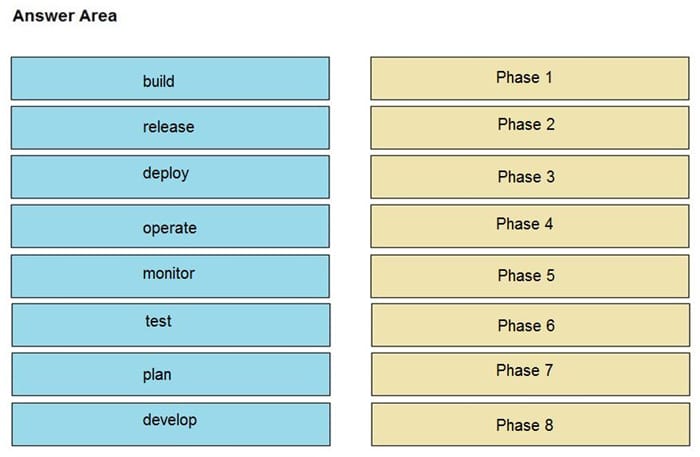
Correct Answer:
Question 4:
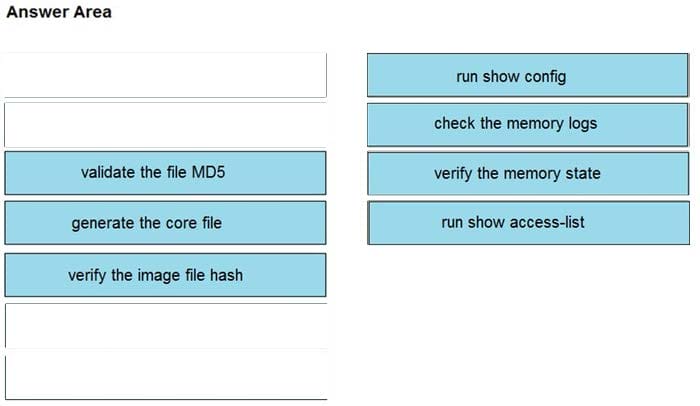
DRAG DROP
An organization lost connectivity to critical servers, and users cannot access business applications and internal websites. An engineer checks the network devices to investigate the outage and determines that all devices are functioning. Drag and drop the steps from the left into the sequence on the right to continue investigating this issue. Not all options are used.
Select and Place:
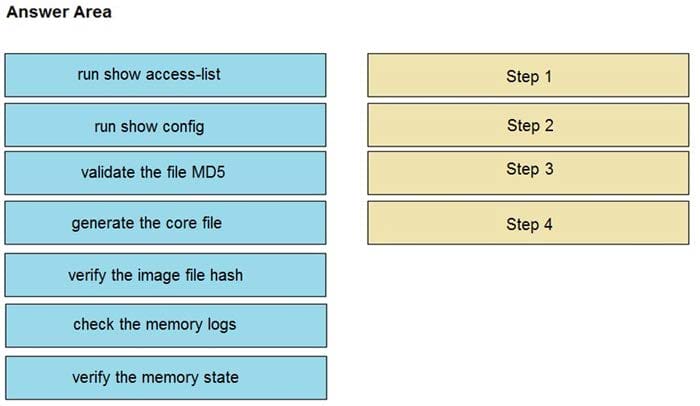
Correct Answer:
Question 5:
Refer to the exhibit. Which indicator of compromise is represented by this STIX?
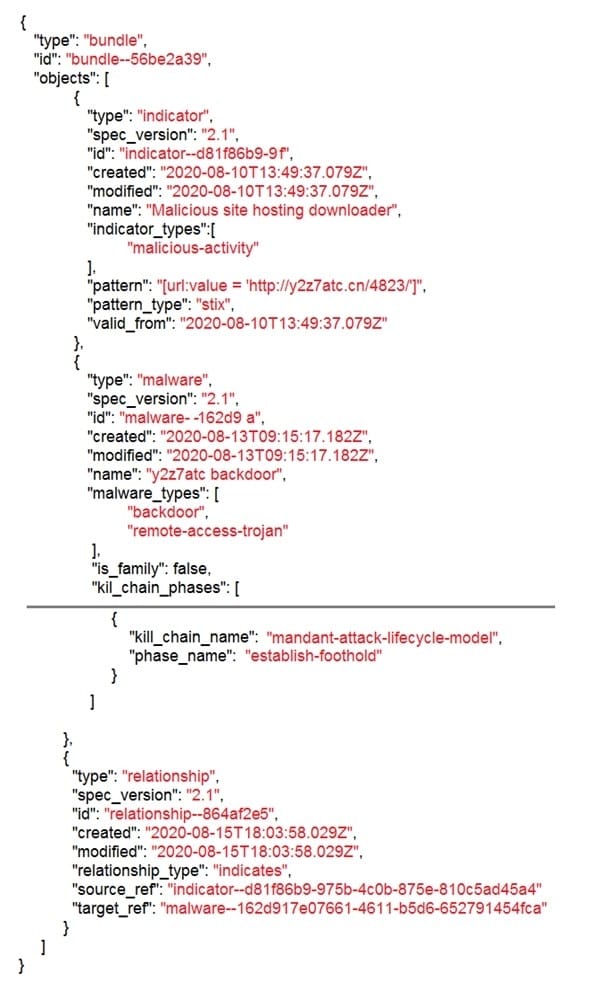
A. website redirecting traffic to ransomware server
B. website hosting malware to download files
C. web server vulnerability exploited by malware
D. cross-site scripting vulnerability to backdoor server
Correct Answer: C
Question 6:
An engineer detects an intrusion event inside an organization\’s network and becomes aware that files that contain personal data have been accessed.
Which action must be taken to contain this attack?
A. Disconnect the affected server from the network.
B. Analyze the source.
C. Access the affected server to confirm compromised files are encrypted.
D. Determine the attack surface.
Correct Answer: C
Question 7:
DRAG DROP
Drag and drop the actions below the image onto the boxes in the image for the actions that should be taken during this playbook step. Not all options are used.
Select and Place:
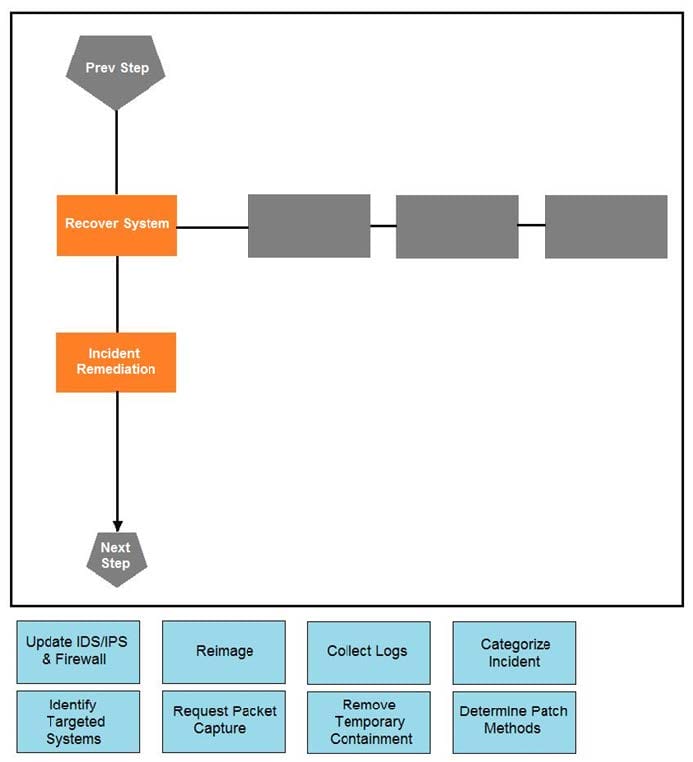
Correct Answer:
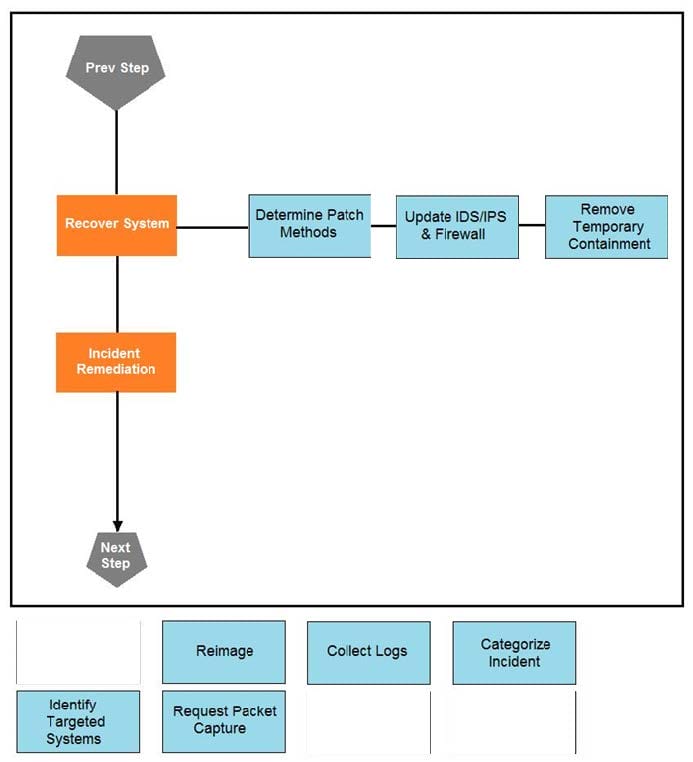
Question 8:
An organization had a breach due to a phishing attack. An engineer leads a team through the recovery phase of the incident response process. Which action should be taken during this phase?
A. Host a discovery meeting and define configuration and policy updates
B. Update the IDS/IPS signatures and reimage the affected hosts
C. Identify the systems that have been affected and tools used to detect the attack
D. Identify the traffic with data capture using Wireshark and review email filters
Correct Answer: C
Question 9:

Refer to the exhibit. An organization is using an internal application for printing documents that requires a separate registration on the website. The application allows format-free user creation, and users must match these required conditions to comply with the company\’s user creation policy: minimum length: 3 usernames can only use letters, numbers, dots, and underscores usernames cannot begin with a number
The application administrator has to manually change and track these daily to ensure compliance. An engineer is tasked to implement a script to automate the process according to the company user creation policy. The engineer implemented this piece of code within the application, but users are still able to create format-free usernames.
Which change is needed to apply the restrictions?
A. modify code to return error on restrictions def return false_user(username, minlen)
B. automate the restrictions def automate_user(username, minlen)
C. validate the restrictions, def validate_user(username, minlen)
D. modify code to force the restrictions, def force_user(username, minlen)
Correct Answer: B
Question 10:
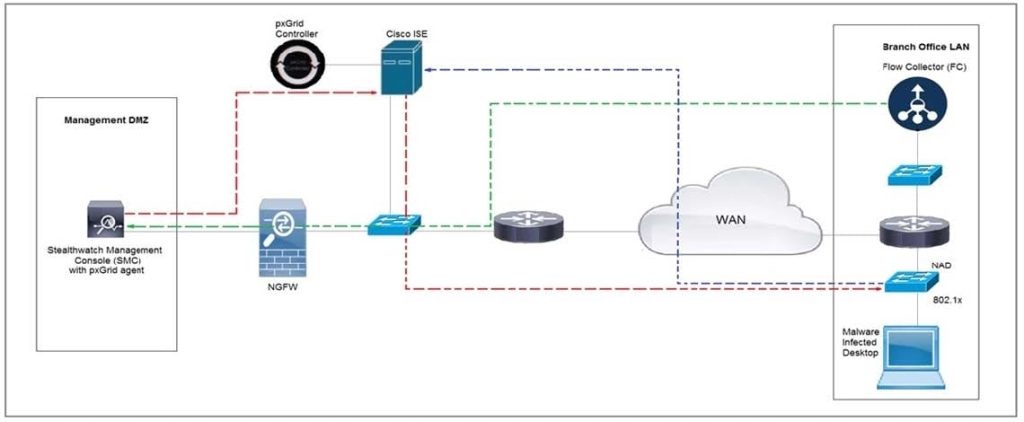
Refer to the exhibit. Cisco Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a Quarantine VLAN using Adaptive Network Control policy.
Which telemetry feeds were correlated with SMC to identify the malware?
A. NetFlow and event data
B. event data and syslog data
C. SNMP and syslog data
D. NetFlow and SNMP
Correct Answer: B
Question 11:
A European-based advertisement company collects tracking information from partner websites and stores it on a local server to provide tailored ads. Which standard must the company follow to safeguard the resting data?
A. HIPAA
B. PCI-DSS
C. Sarbanes-Oxley
D. GDPR
Correct Answer: D
Reference: https://www.thesslstore.com/blog/10-data-privacy-and-encryption-laws-every-business-needs-to-know/
Question 12:
What do 2xx HTTP response codes indicate for REST APIs?
A. additional action must be taken by the client to complete the request
B. the server takes responsibility for error status codes
C. communication of transfer protocol-level information
D. successful acceptance of the client\’s request
Correct Answer: D
Question 13:
DRAG DROP
Drag and drop the mitigation steps from the left onto the vulnerabilities they mitigate on the right.
Select and Place:
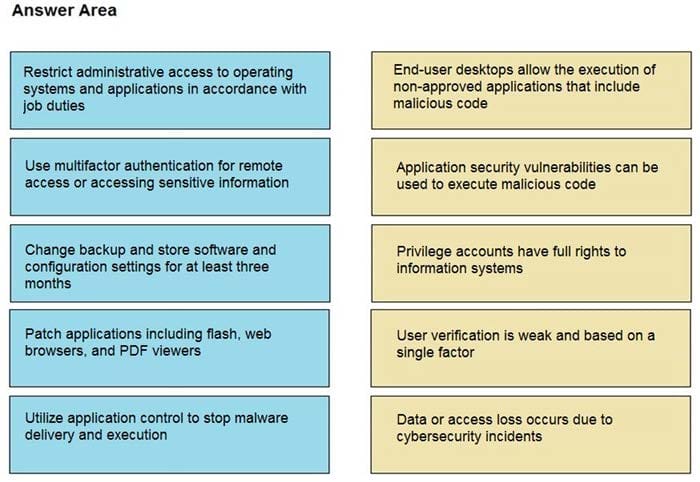
Correct Answer:
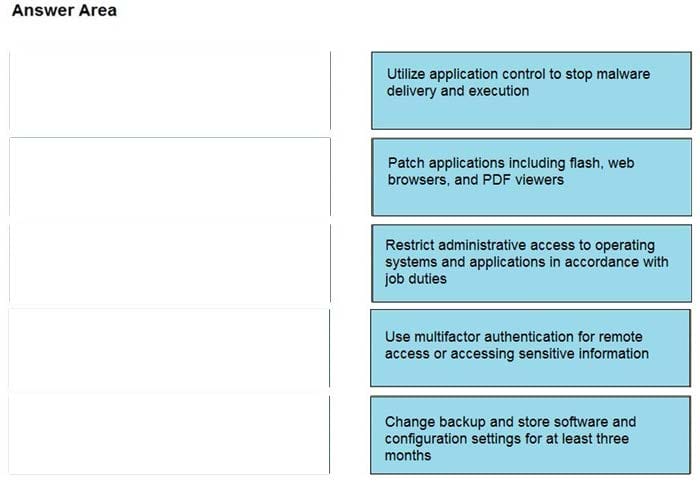
Question 14:
The SIEM tool informs a SOC team of a suspicious file. The team initializes the analysis with an automated sandbox tool, sets up a controlled laboratory to examine the malware specimen, and proceeds with behavioral analysis. What is the next step in the malware analysis process?
A. Perform static and dynamic code analysis of the specimen.
B. Unpack the specimen and perform memory forensics.
C. Contain the subnet in which the suspicious file was found.
D. Document findings and clean-up the laboratory.
Correct Answer: B
Question 15:
An audit is assessing a small business that is selling automotive parts and diagnostic services. Due to increased customer demands, the company recently started to accept credit card payments and acquired a POS terminal. Which compliance regulations must the audit apply to the company?
A. HIPAA
B. FISMA
C. COBIT
D. PCI DSS
Correct Answer: D
Reference: https://upserve.com/restaurant-insider/restaurant-pos-pci-compliance-checklist/
…
Who Should Take the 350-201 CBRCOR Exam in 2025–2026?
This certification is ideal for:
- Security Operations Center (SOC) analysts
- Cybersecurity engineers
- Cloud security analysts
- Security automation specialists
As organizations expand SOC staffing and AI-based detection capabilities, certified professionals are expected to remain in high demand through 2026.
How to Prepare for the 350-201 Exam Efficiently
Use Updated 350-201 Exam Dumps
Rely on realistic, frequently updated dumps so you can practice the newest question patterns.
Build a 30-Day Study Workflow
Break your preparation into:
- Week 1: Threat analysis + Cisco security tools refresher
- Week 2: Cloud incident response + encrypted traffic analytics
- Week 3: Practice with updated dumps
- Week 4: Full-length simulations + weak-area review
Blend Official + Practical Materials
Use Cisco’s official study resources together with 350-201 dumps to cover both theory and real-world scenario practice.
Learn from Cybersecurity Experts
In 2025, SOC tooling evolves monthly. Staying updated through security communities, blogs, or peer groups can significantly improve practical knowledge.
Why Leads4Pass Is a Trusted Source for 350-201 Dumps
Leads4Pass continues leading the market due to:
- Over a decade of industry credibility
- Consistent year-round updates aligned with Cisco’s blueprint
- Verified Q&A accuracy
- A long track record supporting first-attempt passers
You can explore the latest update pack here:
👉 Leads4Pass 350-201 Dumps
Future Outlook for CyberOps Professionals (2026 Forecast)
Cybersecurity hiring trends across the US and Europe indicate:
- Sharp growth in AI-powered SOC environments
- Rising need for cloud-forensics professionals
- Higher budgets for security automation teams
- Competitive salaries for CyberOps Professional holders
This puts CBRCOR candidates in a strong position for 2026 career opportunities.
Conclusion
The Cisco 350-201 CBRCOR certification remains one of the most valuable mid-to-senior-level cybersecurity credentials entering 2026. With updated exam structures and more challenging real-world scenarios, having access to accurate and frequently updated study materials makes a significant difference. Using the latest 350-201 dumps, especially from a reputable source like Leads4Pass, gives you the clarity, confidence, and precision you need to pass on your first attempt.
FAQs
1. Is the 350-201 exam updated for 2025–2026?
Yes, Cisco has refreshed several exam sections, especially cloud security and AI-driven threat analytics.
2. How many questions are on the CBRCOR exam?
The exam currently includes 90–110 questions.
3. Are updated dumps useful for first-attempt success?
Yes—updated dumps help you practice the exact question style and complexity.
4. Is Leads4Pass still reliable in 2025?
Yes, it remains one of the top-rated providers, with verified accuracy and consistent updates.
5. Which roles benefit most from CBRCOR certification?
SOC analysts, incident responders, cloud security engineers, and detection specialists.
 The article concludes by providing
The article concludes by providing 
Recent Comments