
The latest updated Cisco CyberOps Professional 350-201 exam dumps contain PDF and VCE.
All test questions have been corrected and updated to ensure 100% validity. You can practice the actual test questions in the Cisco 350-201 section online first.
For complete Cisco 350-201 exam questions and answers, please visit https://www.leads4pass.com/350-201.html (PDF + VCE) Cisco 350-201 exam “Performing CyberOps Using Cisco Security Technologies (CBRCOR)”.
Cisco CyberOps Professional update notice:
Cisco CyberOps Professional exam series 300-215 is updated! The Cisco CyberOps Professional exam series includes 300-215 CBRFIR, 350-201 CBRCOR. You can search for the latest updated 300-215 exam practice questions at examineeverything.org
[350-201 PDF] Cisco 350-201 pdf free from leads4pass
Free share Cisco 350-201 exam PDF from Vcecert provided by leads4pass
https://www.vcecert.com/wp-content/uploads/2021/07/lead4pass-Cisco-CyberOps-Professional-350-201-Exam-Dumps-Braindumps-PDF-VCE.pdf
[350-201 practice test Q1-Q15] Free sharing of Cisco CyberOps Professional 350-201 exam questions and answers from leads4pass
QUESTION 1
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and availability?
A. Perform a vulnerability assessment
B. Conduct a data protection impact assessment
C. Conduct penetration testing
D. Perform awareness testing
Correct Answer: B
Reference: https://apdcat.gencat.cat/web/.content/03-documentacio/Reglament_general_de_proteccio_de_dades/documents/DPIA-Guide.pdf
QUESTION 2
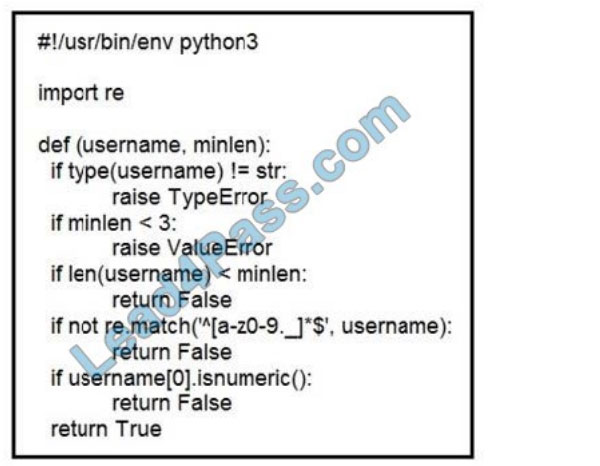
Refer to the exhibit. An organization is using an internal application for printing documents that requires a separate
registration on the website. The application allows format-free user creation, and users must match these required
conditions to comply with the company\\’s user creation policy: minimum length: 3 usernames can only use letters,
numbers, dots, and underscores usernames cannot begin with a number
The application administrator has to manually change and track these daily to ensure compliance. An engineer is tasked
to implement a script to automate the process according to the company user creation policy. The engineer
implemented this piece of code within the application, but users are still able to create format-free usernames.
Which change is needed to apply the restrictions?
A. modify code to return error on restrictions def return false_user(username, minlen)
B. automate the restrictions def automate_user(username, minlen)
C. validate the restrictions, def validate_user(username, minlen)
D. modify code to force the restrictions, def force_user(username, minlen)
Correct Answer: B
QUESTION 3
Refer to the exhibit. An engineer is performing a static analysis on a malware and knows that it is capturing keys and
webcam events on a company server. What is the indicator of compromise?
A. The malware is performing comprehensive fingerprinting of the host, including a processor, motherboard
manufacturer, and connected removable storage.
B. The malware is a ransomware querying for installed anti-virus products and operating systems to encrypt and render
unreadable until payment is made for file decryption.
C. The malware has moved to harvesting cookies and stored account information from major browsers and configuring
a reverse proxy for intercepting network activity.
D. The malware contains an encryption and decryption routine to hide URLs/IP addresses and is storing the output of
loggers and webcam captures in locally encrypted files for retrieval.
Correct Answer: B
QUESTION 4
A malware outbreak is detected by the SIEM and is confirmed as a true positive. The incident response team follows the
playbook to mitigate the threat. What is the first action for the incident response team?
A. Assess the network for unexpected behavior
B. Isolate critical hosts from the network
C. Patch detected vulnerabilities from critical hosts
D. Perform analysis based on the established risk factors
Correct Answer: B
QUESTION 5
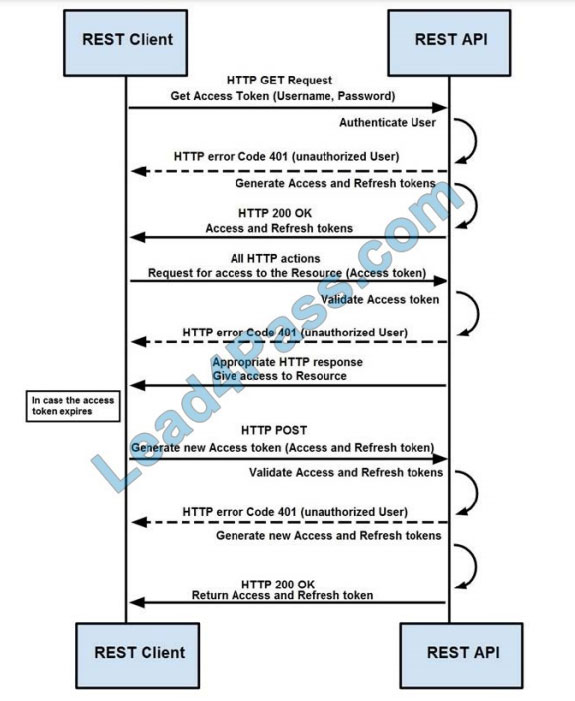
Refer to the exhibit. How are tokens authenticated when the REST API on a device is accessed from a REST API
client?
A. The token is obtained by providing a password. The REST client requests access to a resource using the access
token. The REST API validates the access token and gives access to the resource.
B. The token is obtained by providing a password. The REST API requests access to a resource using the access
token, validates the access token, and gives access to the resource.
C. The token is obtained before providing a password. The REST API provides resource access, refreshes tokens, and
returns them to the REST client. The REST client requests access to a resource using the access token.
D. The token is obtained before providing a password. The REST client provides access to a resource using the access
token. The REST API encrypts the access token and gives access to the resource.
Correct Answer: D
QUESTION 6
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and
service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts
overnight.
Which type of compromise is indicated?
A. phishing
B. dumpster diving
C. social engineering
D. privilege escalation
Correct Answer: C
QUESTION 7
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type
of copy and paste attempts of sensitive data within unapproved applications and removable devices. Which technical
architecture must be used?
A. DLP for data in motion
B. DLP for removable data
C. DLP for data in use
D. DLP for data at rest
Correct Answer: C
Reference: https://www.endpointprotector.com/blog/what-is-data-loss-prevention-dlp/
QUESTION 8
Refer to the exhibit. IDS is producing an increased amount of false positive events about brute force attempts on the
organization\\’s mail server. How should the Snort rule be modified to improve performance?
A. Block list of internal IPs from the rule
B. Change the rule content match to case sensitive
C. Set the rule to track the source IP
D. Tune the count and seconds threshold of the rule
Correct Answer: B
QUESTION 9
What is a limitation of cyber security risk insurance?
A. It does not cover the costs to restore stolen identities as a result of a cyber attack
B. It does not cover the costs to hire forensics experts to analyze the cyber attack
C. It does not cover the costs of damage done by third parties as a result of a cyber attack
D. It does not cover the costs to hire a public relations company to help deal with a cyber attack
Correct Answer: A
Reference: https://tplinsurance.com/products/cyber-risk-insurance/
QUESTION 10
Refer to the exhibit. A security analyst needs to investigate a security incident involving several suspicious connections
with a possible attacker. Which tool should the analyst use to identify the source IP of the offender?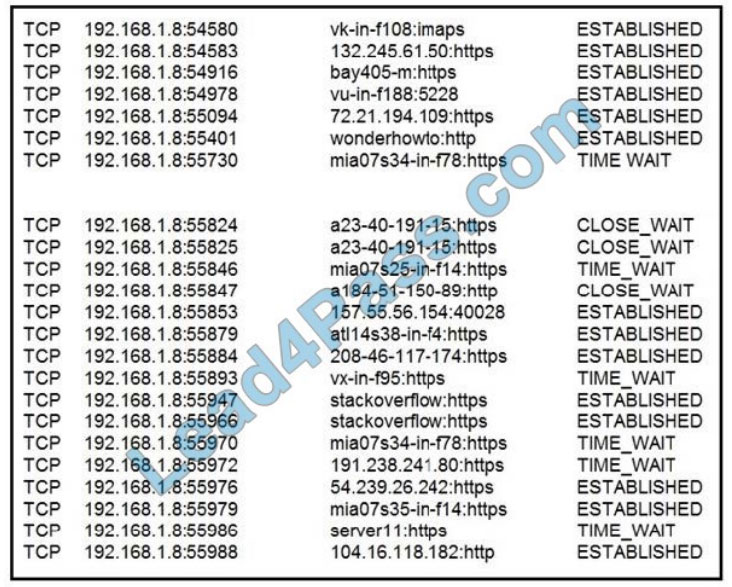
A. packet sniffer
B. malware analysis
C. SIEM
D. firewall manager
Correct Answer: A
QUESTION 11
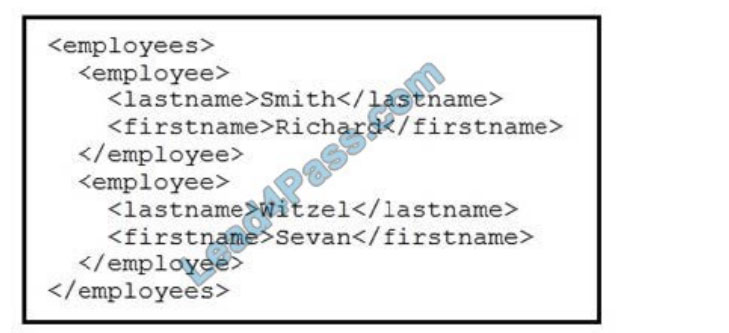
Refer to the exhibit. Which data format is being used?
A. JSON
B. HTML
C. XML
D. CSV
Correct Answer: B
QUESTION 12
Refer to the exhibit. Where does it signify that a page will be stopped from loading when a scripting attack is detected?
A. x-frame-options
B. x-content-type-options
C. x-xss-protection
D. x-test-debug
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/customize-http-security-headersad-fs
QUESTION 13
An organization installed a new application server for IP phones. An automated process fetched user credentials from
the Active Directory server, and the application will have access to on-premises and cloud services. Which security
threat should be mitigated first?
A. aligning access control policies
B. exfiltration during data transfer
C. attack using default accounts
D. data exposure from backups
Correct Answer: B
QUESTION 14
A customer is using a central device to manage network devices over SNMPv2. A remote attacker caused a denial of
service condition and can trigger this vulnerability by issuing a GET request for the ciscoFlashMIB OID on an affected
device.
Which should be disabled to resolve the issue?
A. SNMPv2
B. TCP small services
C. port UDP 161 and 162
D. UDP small services
Correct Answer: A
Reference: https://nvd.nist.gov/vuln/detail/CVE-2018-0161
QUESTION 15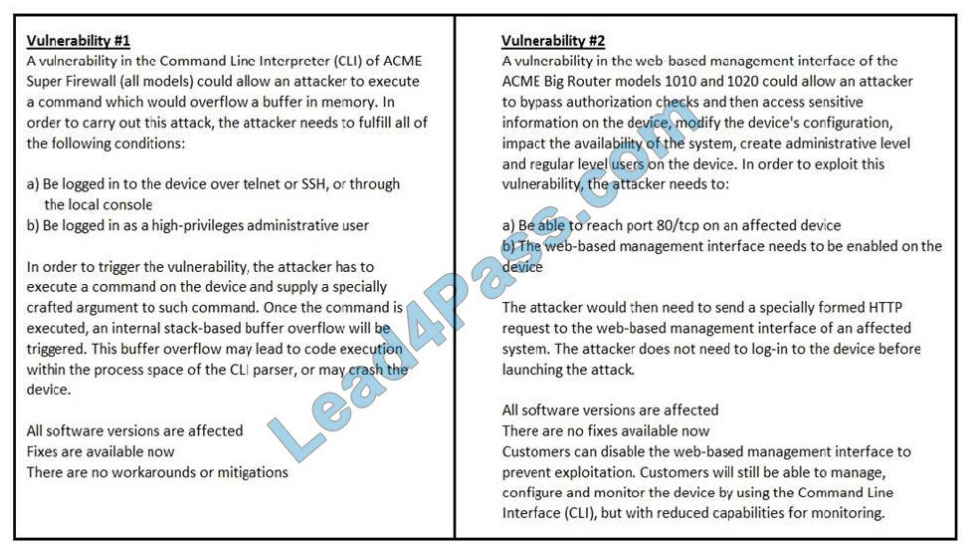
Refer to the exhibit. How must these advisories be prioritized for handling?
A. The highest priority for handling depends on the type of institution deploying the devices
B. Vulnerability #2 is the highest priority for every type of institution
C. Vulnerability #1 and vulnerability #2 have the same priority
D. Vulnerability #1 is the highest priority for every type of institution
Correct Answer: D
leads4pass updates Cisco 350-201 exam questions and answers throughout the year! All exam questions are updated and corrected in real-time by Cisco experts.
Guaranteed to be true and effective! leads4pass has the most complete exam policy! To pass the Cisco 350-201 exam 100%, please click https://www.leads4pass.com/350-201.html (Total Questions: 102 Q&A) leads4pass Cisco Braindumps is trustworthy! I wish you success!
[350-201 PDF] Get free Cisco 350-201 exam PDF online: https://www.vcecert.com/wp-content/uploads/2021/07/lead4pass-Cisco-CyberOps-Professional-350-201-Exam-Dumps-Braindumps-PDF-VCE.pdf

Recent Comments