
leads4pass 200-201 dumps provide candidates with up-to-date and valid exam materials! And with PDF and VCE two learning formats, they both contain the latest exam questions and answers, you can choose arbitrarily!
Download 200-201 dumps with PDF and VCE: https://www.leads4pass.com/200-201.html (264 Q&A), practice test all actual exam questions, and provide difficult problem annotations to help you really master all exams gist, Make sure you pass the exam with ease.
What’s more, leads4pass 200-201 dumps share some latest exam practice questions for free:
| Type | Number of exam questions | Exam name | Exam code | Last updated |
| Free | 13 | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | 200-201 | 200-201 CBROPS dumps |
QUESTION 1:
Refer to the exhibit.
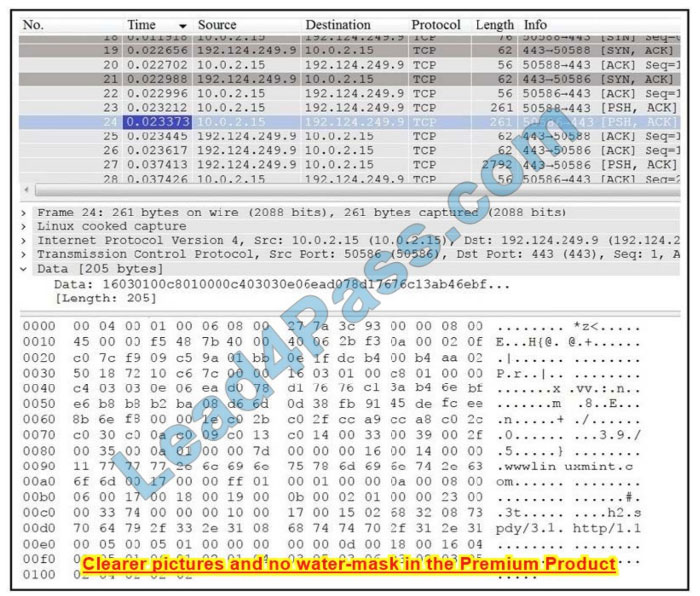
Which application protocol is in this PCAP file?
A. SSH
B. TCP
C. TLS
D. HTTP
Correct Answer: D
QUESTION 2:
What is an example of social engineering attack?
A. receiving an unexpected email from an unknown person with an attachment from someone in the same company
B. receiving an email from human resources requesting a visit to their secure website to update contact information
C. sending a verbal request to an administrator who knows how to change an account password
D. receiving an invitation to the department\’s weekly WebEx meeting
Correct Answer: C
QUESTION 3:
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A. Untampered images are used in the security investigation process
B. Tampered images are used in the security investigation process
C. The image is tampered with if the stored hash and the computed hash match
D. Tampered images are used in the incident recovery process E. The image is untampered if the stored hash and the
computed hash match
Correct Answer: AE
Cert Guide by Omar Santos, Chapter 9 – Introduction to Digital Forensics. “When you collect evidence, you must protect
its integrity. This involves making sure that nothing is added to the evidence and that nothing is deleted or destroyed
(this is known as evidence preservation).”
QUESTION 4:
Refer to the exhibit.
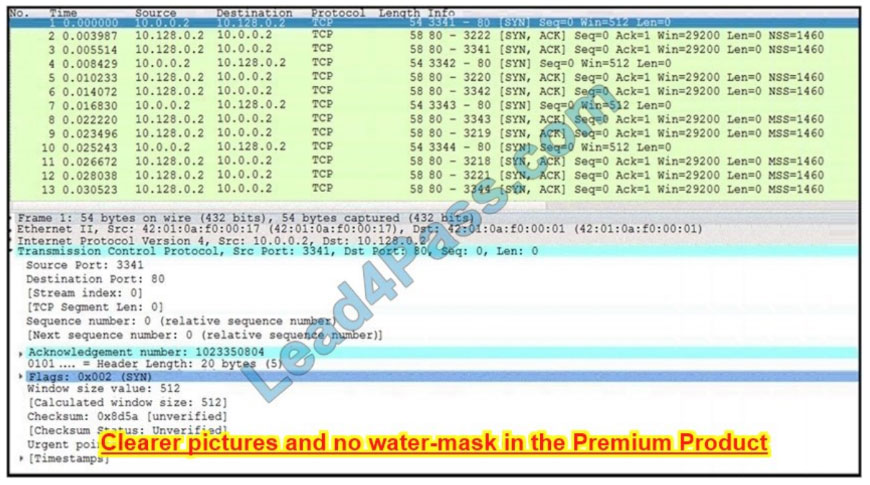
What is occurring in this network traffic?
A. High rate of SYN packets being sent from multiple sources towards a single destination IP.
B. High rate of ACK packets being sent from a single source IP towards multiple destination IPs.
C. Flood of ACK packets coming from a single source IP to multiple destination IPs.
D. Flood of SYN packets coming from a single source IP to a single destination IP.
Correct Answer: D
QUESTION 5:
Which two elements are used for profiling a network? (Choose two.)
A. session duration
B. total throughput
C. running processes
D. listening ports
E. OS fingerprint
Correct Answer: AB
A network profile should include some important elements, such as the following:
Total throughput is the amount of data passing from a given source to a given destination in a given period of time Session
duration of the time between the establishment of a data flow and its termination Ports used a list of TCP or UDP processes that are available to accept data Critical asset address space is the IP addresses or the logical location of essential systems or data Profiling data are data that the system has gathered, these data help for incident response and to detect incident Network profiling = throughput, sessions duration, the port used, Critical Asset Address Space Host profiling = Listening ports, logged-in accounts, running processes, running tasks, applications
QUESTION 6:
Which two components reduce the attack surface on an endpoint? (Choose two.)
A. secure boot
B. load balancing
C. increased audit log levels
D. restricting USB ports
E. full packet captures at the endpoint
Correct Answer: AD
QUESTION 7:
Refer to the exhibit.

Which event is occurring?
A. A binary named “submit” is running on VM cuckoo1.
B. A binary is being submitted to run on VM cuckoo1
C. A binary on VM cuckoo1 is being submitted for evaluation
D. A URL is being evaluated to see if it has a malicious binary
Correct Answer: B
https://cuckoo.readthedocs.io/en/latest/usage/submit/
QUESTION 8:
Refer to the exhibit.
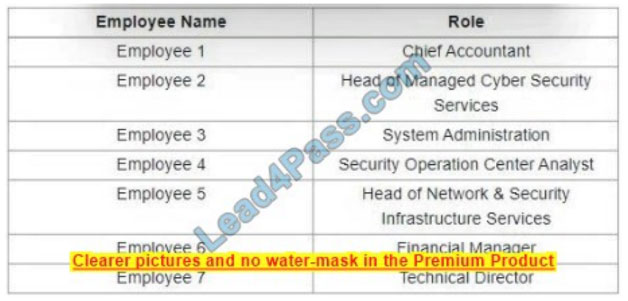
Which stakeholders must be involved when a company workstation is compromised?
A. Employee 1 Employee 2, Employee 3, Employee 4, Employee 5, Employee 7
B. Employee 1, Employee 2, Employee 4, Employee 5
C. Employee 4, Employee 6, Employee 7
D. Employee 2, Employee 3, Employee 4, Employee 5
Correct Answer: D
QUESTION 9:
Refer to the exhibit.
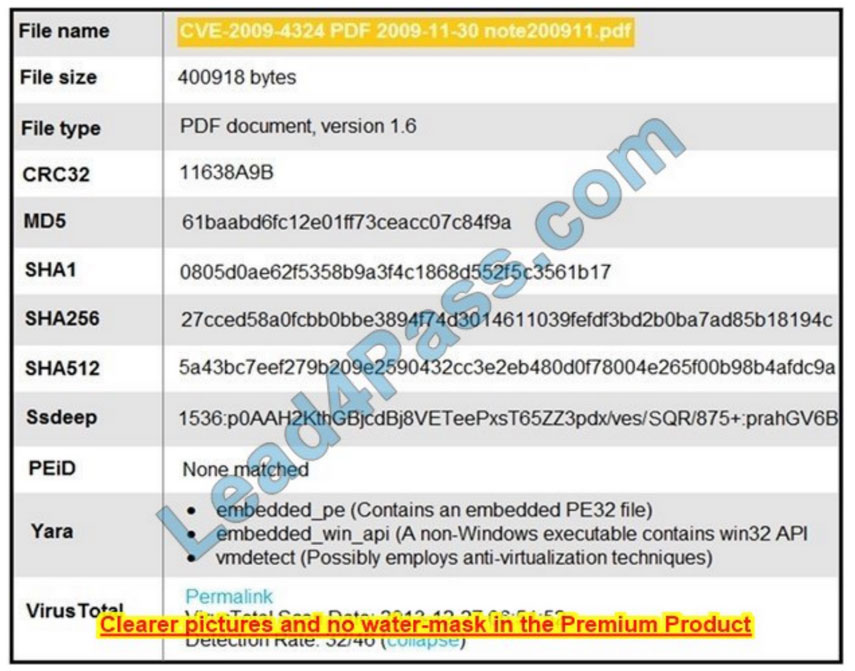
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is
the state of this file?
A. The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
B. The file has an embedded non-Windows executable but no suspicious features are identified.
C. The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
D. The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up
to date.
Correct Answer: C
QUESTION 10:
Which incidence response step includes identifying all hosts affected by an attack?
A. detection and analysis
B. post-incident activity
C. preparation
D. containment, eradication, and recovery
Correct Answer: D
3.3.3 Identifying the Attacking Hosts During incident handling, system owners and others sometimes want to or need to
identify the attacking host or hosts. Although this information can be important, incident handlers should generally stay
focused on containment, eradication, and recovery.
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
The response phase, or containment, of incident response, is the point at which the incident response team begins
interacting with affected systems and attempts to keep further damage from occurring as a result of the incident.
QUESTION 11:
What is the difference between the ACK flag and the RST flag?
A. The RST flag approves the connection, and the ACK flag terminates spontaneous connections.
B. The ACK flag confirms the received segment, and the RST flag terminates the connection.
C. The RST flag approves the connection, and the ACK flag indicates that a packet needs to be resent
D. The ACK flag marks the connection as reliable, and the RST flag indicates the failure within TCP Handshake
Correct Answer: B
QUESTION 12:
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
A. The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the
payload is complete
B. The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the
payload is complete
C. The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a
connection
D. The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a
connection
Correct Answer: D
QUESTION 13:
Which vulnerability type is used to read, write, or erase information from a database?
A. cross-site scripting
B. cross-site request forgery
C. buffer overflow
D. SQL injection
Correct Answer: D
…
PS. Download the latest 200-201 exam practice questions above: https://drive.google.com/file/d/1UjWu1pun-sCnyJo0Js9K_8jZcvV3bmPI/
Take this practice session to learn some of the latest 200-201 exam facts! Improve your strength!
Now, use 200-201 dumps with PDF and VCE: https://www.leads4pass.com/200-201.html (264 Q&A), to help you pass the exam 100% successfully.

Recent Comments