![[Aug 2025] Leads4Pass 200-201 dumps](https://www.vcecert.com/wp-content/uploads/2025/08/update-aug-2025-200-201-dumps-1024x410.jpg)
The 2025 August update of the 200-301 dumps: https://www.leads4pass.com/200-201.html, compared to the May 2023 update of the 200-301 dumps, includes over 100 new exam questions and answers. Moreover, all practice questions have been comprehensively updated to align with the 2025 CyberOps Associate certification exam plan.
Come on! Try the online practice test:
Latest 200-201 dumps practice questions free share
| Related | Tip | From |
| CyberOps Associate | We freely share the latest practice questions for each iteration. | Leads4Pass |
Question 1:
What are two social engineering techniques? (Choose two.)
A. privilege escalation
B. DDoS attack
C. phishing
D. man-in-the-middle
E. pharming
Correct Answer: CE
Question 2:
An engineer received a flood of phishing emails from HR with the source address HRjacobm@companycom. What is the threat actor in this scenario?
A. phishing email
B. sender
C. HR
D. receiver
Correct Answer: B
Question 3:
Which security monitoring data type requires the largest storage space?
A. transaction data
B. statistical data
C. session data
D. full packet capture
Correct Answer: D
Question 4:
How does certificate authority impact a security system?
A. It authenticates client identity when requesting SSL certificate
B. It validates domain identity of a SSL certificate
C. It authenticates domain identity when requesting SSL certificate
D. It validates client identity when communicating with the server
Correct Answer: B
Question 5:
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
A. known-plaintext
B. replay
C. dictionary
D. man-in-the-middle
Correct Answer: D
Question 6:
An engineer configured regular expression “.*\.([Dd][Oo][Cc]|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1.[01]” on Cisco ASA firewall. What does this regular expression do?
A. It captures .doc, .xls, and .pdf files in HTTP v1.0 and v1.1.
B. It captures documents in an HTTP network session.
C. It captures Word, Excel, and PowerPoint files in HTTP v1.0 and v1.1.
D. It captures .doc, .xls, and .ppt files extensions in HTTP v1.0.
Correct Answer: C
Explanation:
The regular expression pattern captures file extensions like .doc, .xls, and .ppt (or variations in letter case, such as DOC, XLS, PPT) within HTTP traffic sessions, as indicated by the “.([Dd][Oo][Cc]|[Xx][LI][Ss]|[Pp][Pp][Tt])” part of the regex.
Additionally, it specifies HTTP versions 1.0 and 1.1 by ending with ” HTTP/1.[01]” to focus the matching on HTTP sessions using these versions.
Question 7:
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
A. ransomware communicating after infection
B. users downloading copyrighted content
C. data exfiltration
D. user circumvention of the firewall
Correct Answer: D
Question 8:
Which two elements are used for profiling a network? (Choose two.)
A. session duration
B. total throughput
C. running processes
D. listening ports
E. OS fingerprint
Correct Answer: AB
A network profile should include some important elements, such as the following:
Total throughput the amount of data passing from a given source to a given destination in a given period of time Session duration the time between the establishment of a data flow and its termination Ports used a list of TCP or UDP processes that are available to accept data Critical asset address space the IP addresses or the logical location of essential systems or data Profiling data are data that system has gathered, these data helps for incident response and to detect incident Network profiling = throughput, sessions duration, port used, Critical Asset Address Space Host profiling = Listening ports, logged in accounts, running processes, running tasks,applications
Question 9:
What is a sandbox interprocess communication service?
A. A collection of rules within the sandbox that prevent the communication between sandboxes.
B. A collection of network services that are activated on an interface, allowing for inter-port communication.
C. A collection of interfaces that allow for coordination of activities among processes.
D. A collection of host services that allow for communication between sandboxes.
Correct Answer: C
Inter-process communication (IPC) allows communication between different processes. A process is one or more threads running inside its own, isolated address space. https://docs.legato.io/16_10/basicIPC.html
Question 10:
Refer to the exhibit.
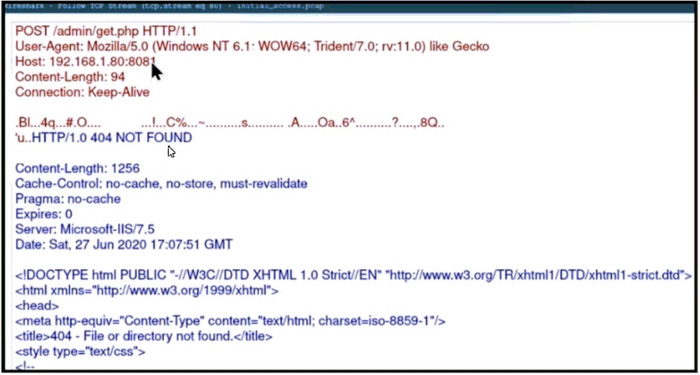
A security analyst received a ticket about suspicious traffic from one of the workstations. During the investigation, the analyst discovered that the workstation is communicating with an external IP The analyst was not able to investigate further and escalated the case to a T2 security analyst. What are the two data visibility challenges that the security analyst should identify? (Choose two.)
A. A default user agent is present in the headers.
B. Traffic is not encrypted.
C. Encrypted data is being transmitted.
D. POST requests have a “Microsoft-IIS/7.5” server header.
E. HTTP requests and responses are sent in plaintext.
Correct Answer: BE
Question 11:
Refer to the exhibit.
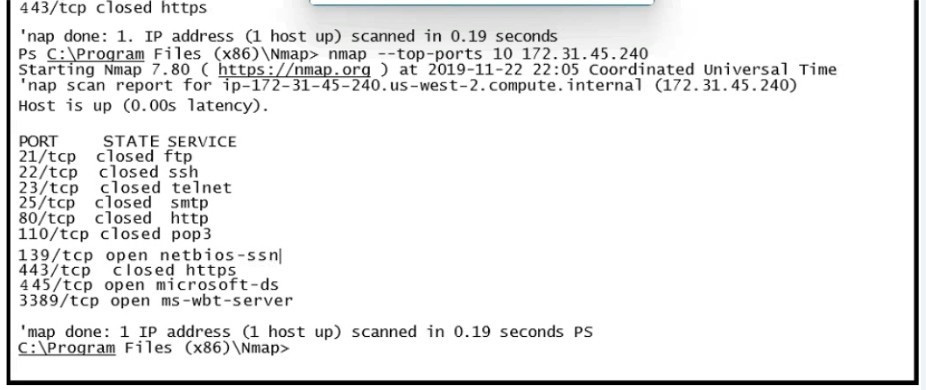
What does this output indicate?
A. HTTPS ports are open on the server.
B. SMB ports are closed on the server.
C. FTP ports are open on the server.
D. Email ports are closed on the server.
Correct Answer: D
Question 12:
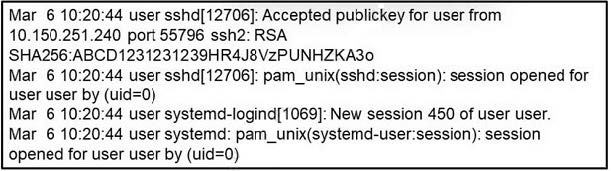
Refer to the exhibit. What occurred on this system based on this output?
A. A user connected to the system using remote access VPN.
B. A user connected to the system after 450 attempts.
C. A user connected to the system using SSH using source port 55796.
D. A user created a new HTTP session using the SHA256 hashing algorithm.
Correct Answer: C
Question 13:
Which security principle requires more than one person is required to perform a critical task?
A. least privilege
B. need to know
C. separation of duties
D. due diligence
Correct Answer: C
Question 14:
A security engineer notices confidential data being exfiltrated to a domain “Ranso4134- mware31-895” address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Cyber Kill Chain?
A. reconnaissance
B. delivery
C. action on objectives
D. weaponization
Correct Answer: D
Question 15:
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
A. social engineering
B. eavesdropping
C. piggybacking
D. tailgating
Correct Answer: A
The above is the latest free share of Cisco 200-201 practice questions and answers for August 2025. Once again, we emphasize not to waste time practicing hundreds or thousands of outdated and invalid exam questions, as they will only waste your time. Truly valuable resources are not free. You are welcome to download the latest Cisco 200-201 dumps: https://www.leads4pass.com/200-201.html, which includes 438 practice questions and answers, ensuring a 100% pass rate for the exam.

Recent Comments